![]()
[update March 3, 2025]
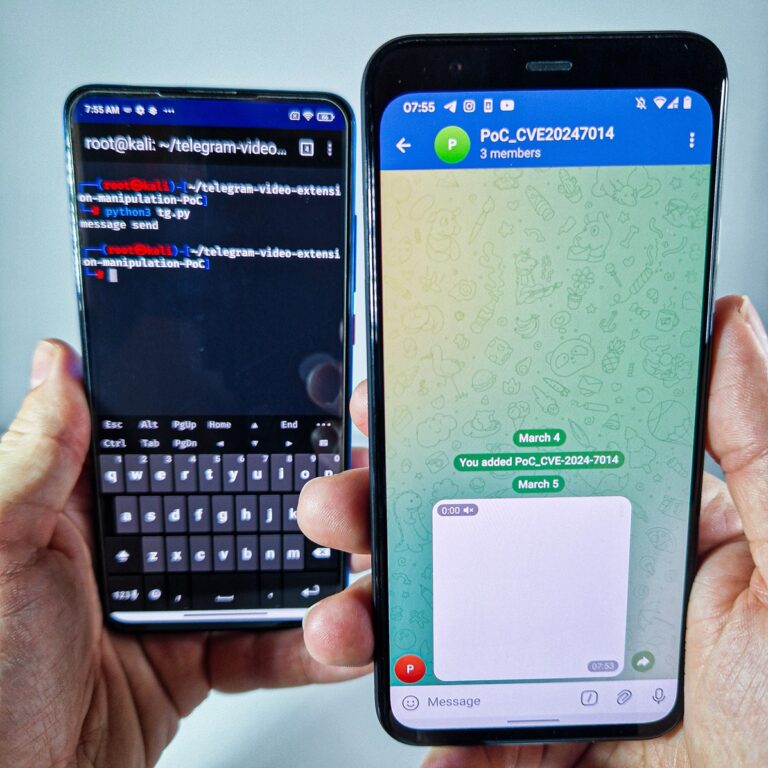
On Mar 6, 2025 Telegram patched the EvilLoader vulnerability on server side. I verified that issue is fixed now. Telegram promptly fixed it within 48 hours from my report.
A newly discovered vulnerability in Telegram for Android, dubbed EvilLoader, has been identified by malware and CTI analyst 0x6rss. This exploit allows attackers to disguise malicious APKs as video files, potentially leading to unauthorized malware installations on users’ devices. The vulnerability was detailed in his blog post and accompanied by a Proof of Concept (PoC) code. This exploit remains unpatched and continues to work on the latest version of Telegram for Android 11.7.4. Even more concerning, the payload has been available for sale on underground forums since January 15, 2025, making it accessible to cybercriminals worldwide. This is similar to WhatsApp trick, where Android malware can impersonate PDF file and trick user to install it.
I notified Telegram at [email protected] about this vulnerability and available PoC on March 04, 2025, but given the urgency of the issue and the fact that it remains exploitable—and has already been sold on underground forums for almost two months—I decided to publish this blog to raise awareness before an official fix is released.
This is the second time a similar vulnerability has been discovered targeting Telegram for Android. The first one, called EvilVideo, was disclosed in July 2024 and tracked as CVE-2024-7014. EvilVideo operated in the same way as EvilLoader, allowing attackers to manipulate video files to deliver malicious APKs. It was also actively sold on underground forums. You can see video of exploitation using the PoC below.
Understanding the EvilLoader Vulnerability
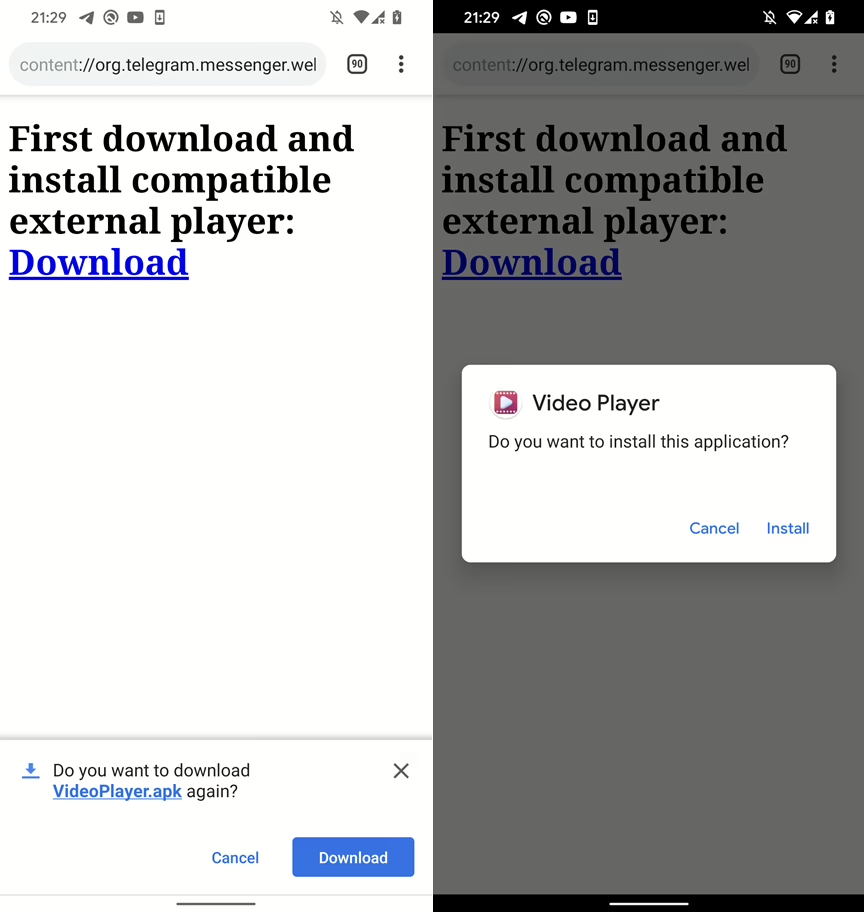
EvilLoader manipulates Telegram’s handling of video files, allowing malicious app to be automatically downloaded and executed under the guise of media content. When a user attempts to play one of these specially crafted “videos,” Telegram prompts them to open the file in an external application, see Figure 1.
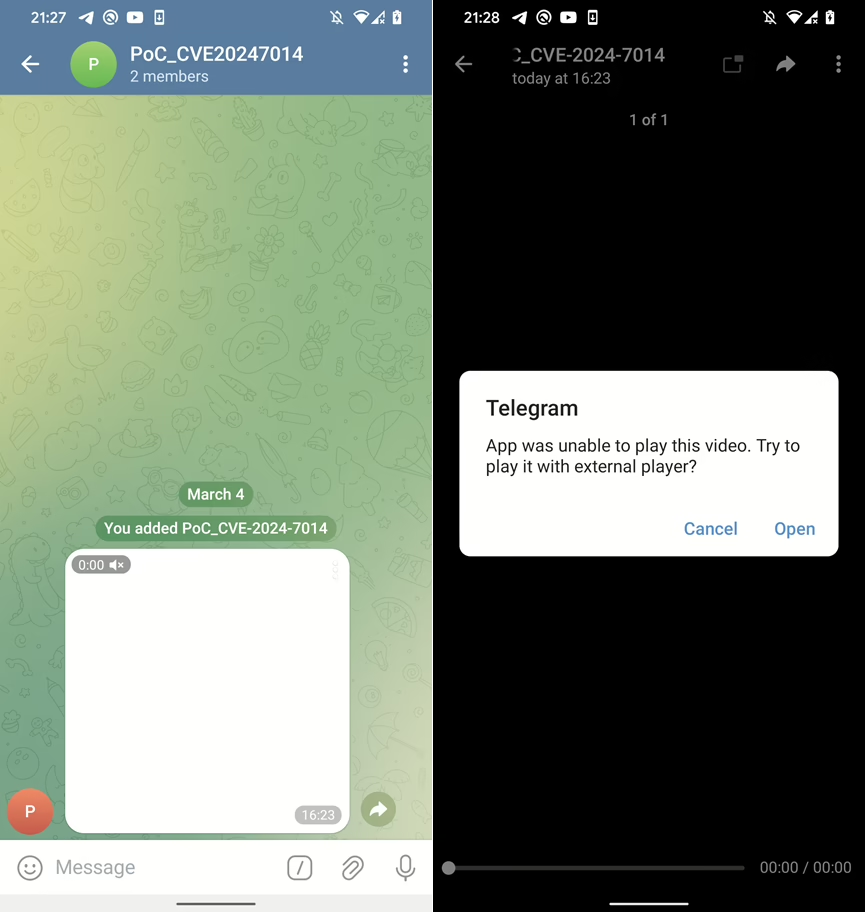
If user selects Cancel, then it would appear as video can’t be played correctly, see Figure 2.

If the user agrees, the disguised APK gets installed, potentially compromising the device.
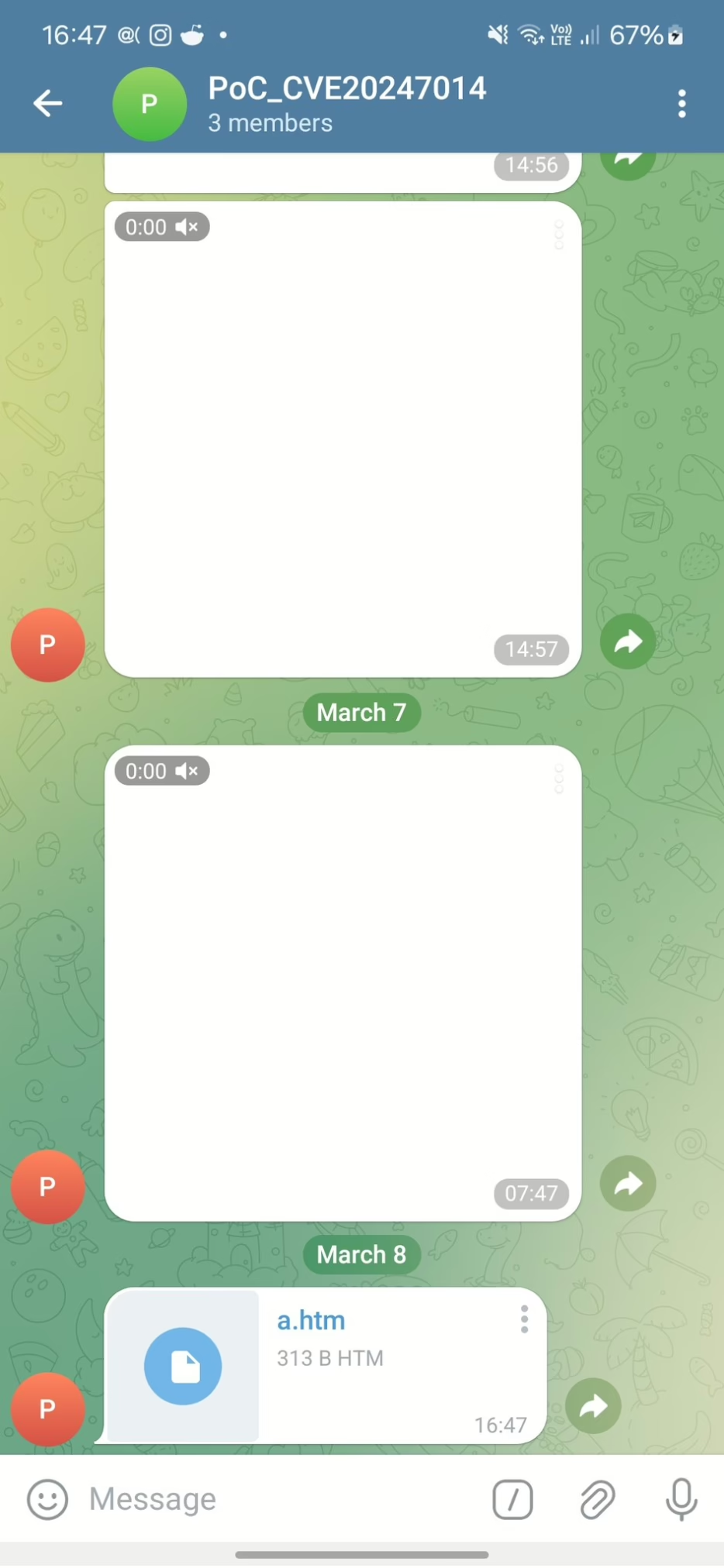
This is achieved by tricking Telegram into handling an HTML file as a video file. A key part of the attack involves crafting an HTML file that Telegram misinterprets as a valid video file, see Figure 3.
Core issue is in an HTML file is created and saved with an MP4 extension, causing Telegram to mistakenly identify it as a video file due to its extension. When sent via Telegram, it is treated as a legitimate media file, and upon opening, the user is prompted to launch it in an external application, at which point malicious code can be executed.
Before the malicious application is installed, the user must explicitly enable the installation of unknown apps on their Android device. When attempting to install the disguised video file, Telegram will prompt the user to install an external application. As part of this process, the user will be required to grant permission for the installation of apps from unknown sources, a security setting that is typically disabled by default to prevent unauthorized installations.
By exploiting Telegram’s inability to correctly validate media files, attackers can embed harmful payloads that appear as harmless video files.
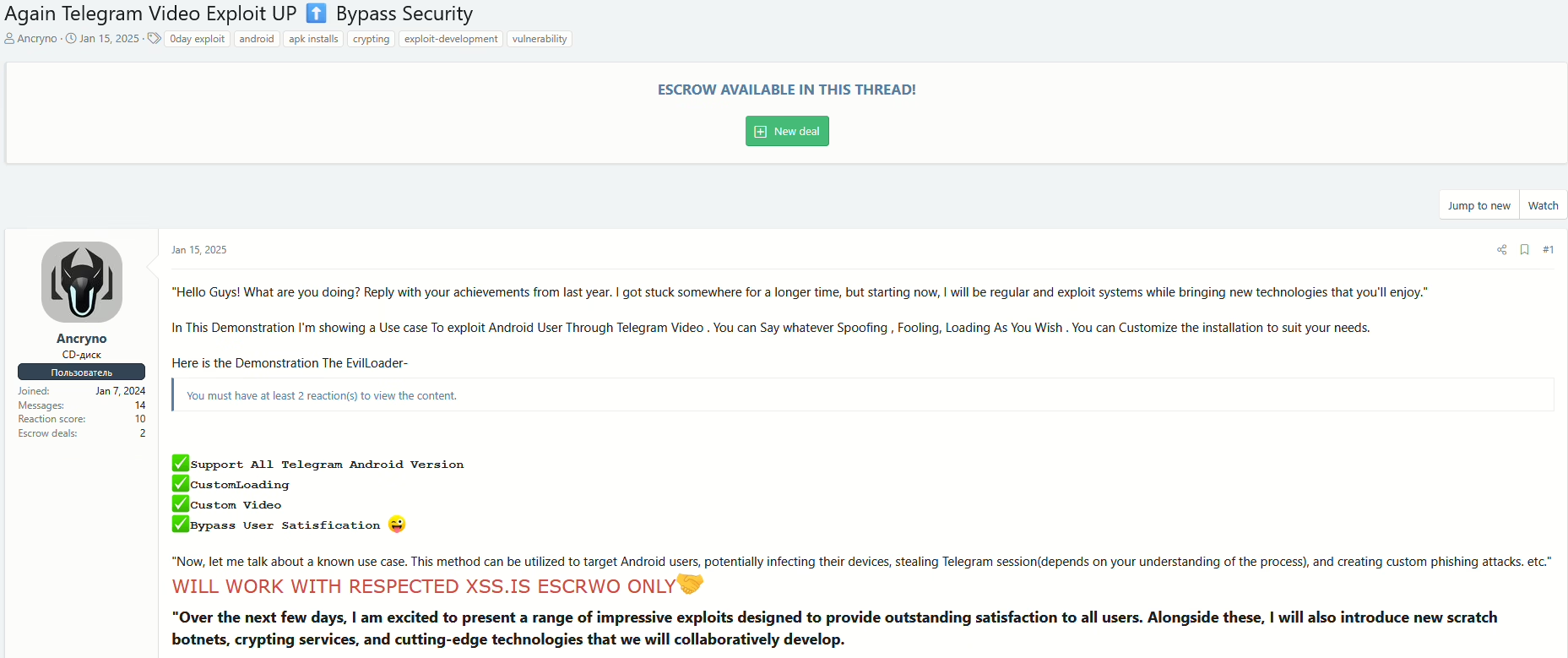
The Exploit is Actively Sold on Underground Forums
Since January 15, 2025, the payload for EvilLoader has been up for sale on an underground forum for unknown price. Cybercriminals have been referring to it as EvilLoader, instead of its initial name EvilVideo. The availability of this exploit on underground marketplaces raises concerns about its widespread abuse, as threat actors can now easily obtain and deploy it against unsuspecting Telegram users.
Why This is a Serious Threat
- The vulnerability remains unpatched in the latest Telegram for Android version, making all users susceptible.
- Attackers can exploit this flaw to deploy spyware, ransomware, or other malware.
- Since Telegram is widely trusted, users may not hesitate to open files received from seemingly legitimate sources.
How to Protect Yourself
Until Telegram addresses this issue, users should take the following precautions:
- Update Telegram: While a patch is pending, stay alert for security updates from Telegram.
- Disable Auto-Download: Prevent media files from downloading automatically in Telegram settings.
- Avoid Untrusted Media Files: Do not open or execute files from unknown sources, especially videos requiring external apps.
- Use Security Software: Install reputable mobile security software that detects malicious APKs.
Conclusion
Given that the exploit remains unfixed and has been actively sold on underground forums, Telegram users must exercise caution when handling media files. The accessibility of this exploit to cybercriminals makes it a serious risk.