![]()
As mobile hackers, we often find that our smartphones, while powerful in many ways, lack the essential radio frequency (RF) features needed for wireless security testing. These limitations can be frustrating when trying to explore wireless signals directly from our mobile devices. However, with the Evil Crow RF V2, these limitations can be easily overcome. This tool expands your smartphone’s capabilities, allowing you to dive into RF analysis, penetration testing, and signal manipulation—bringing mobile hacking to a whole new level.
This compact, portable device can be operated via a smartphone, making it an ideal gadget for cybersecurity enthusiasts on the go. I have received this Sub-GHz gadget to test and play around with it from Krystian, one of owners of Sapsan Cybersec & Military store. My goal was to make it as compact as possible, portable, and fully managed by a smartphone, without need of a computer, raspberry pie, external battery or other extra device. On top of that, with specific firmware, it is compatible with Flipper Zero .sub file format, which means it can replay all the prerecorded frequencies available for unofficial Flipper Zero firmware, which is impressive. This blog explains capabilities and use cases of Evil Crow RF V2, I will compare it to other RF gadgets and share my insights of using it.
Disclaimer
This blog post is intended for educational purposes only and is aimed at professionals in the field of cybersecurity. The information provided here is meant to enhance understanding and knowledge of RF hacking tools and techniques. The use of the Evil Crow RF V2 and similar devices should be conducted responsibly and ethically, in compliance with all applicable laws and regulations. Unauthorized use of these tools for malicious purposes is illegal and unethical. The author and publisher of this blog are not responsible for any misuse of the information provided.
What is the Evil Crow RF V2?
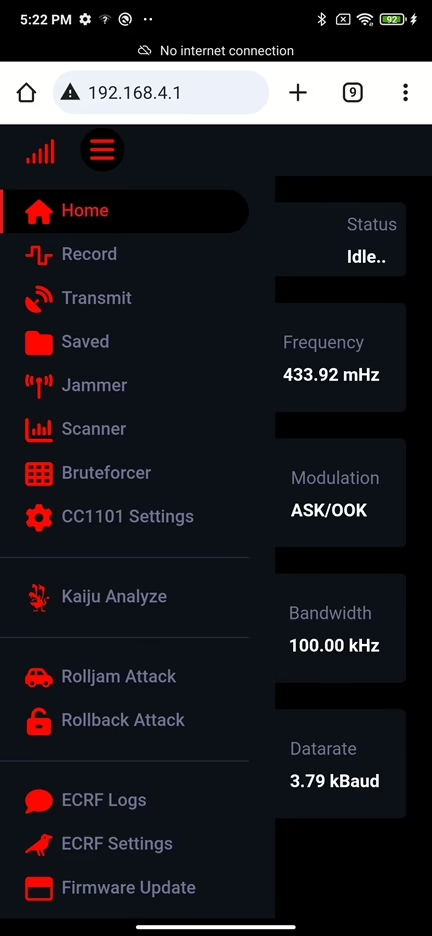
The Evil Crow RF V2 is a pocketsize radio frequency (RF) hacking device designed for penetration testing and Red Team operations created by Joel Serna Moreno. It operates across multiple RF bands, however within Sub-GHz range, such as 300MHz-348MHz, 387MHz-464MHz, 779MHz-928MHz, and 2.4GHz. This ranges typically cover key fobs, gates, ACs, doorbells, garage doors, restaurant pagers, weather stations etc. This device is equipped with two CC1101 RF modules, allowing it to transmit and receive signals on different frequencies simultaneously. Additionally, it features an NRF24L01 module.
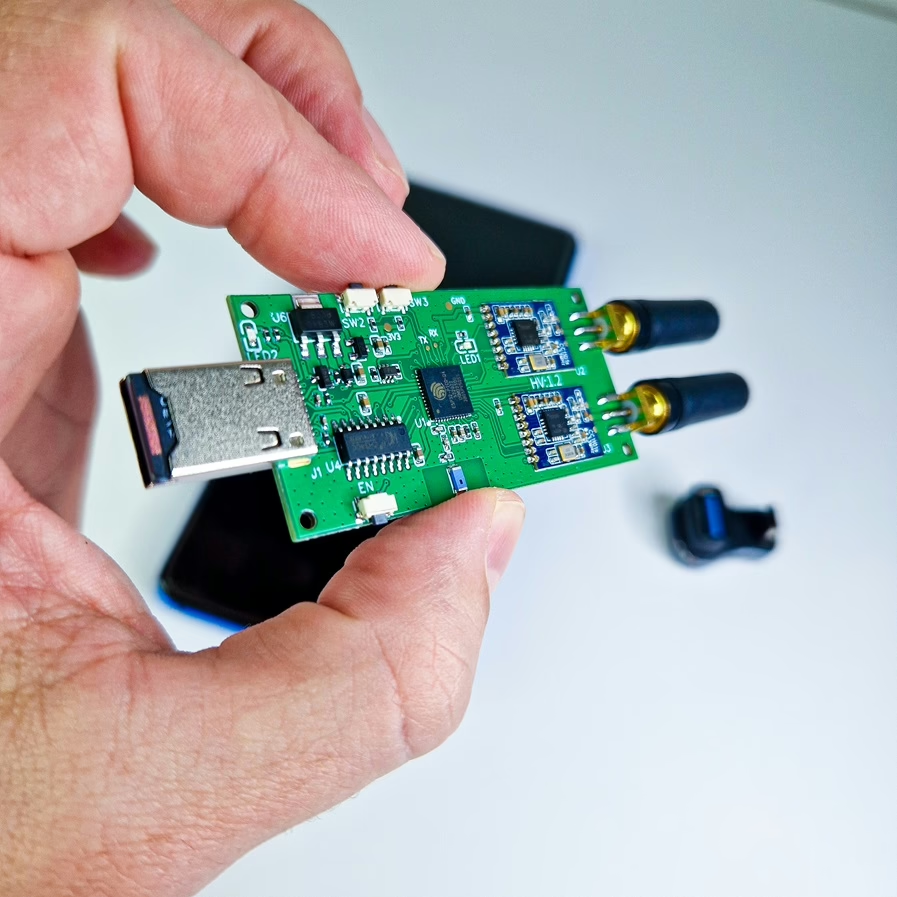
The Evil Crow RF V2 allows users to perform a variety of tasks and attacks, including:
- Receive signal
- Transmit signal
- Replay attacks
- Bruteforce
- Jamming
- Scanner
- Mousejacking
- Rolljam attack
- Rollback attack
- Kaiju analyzer (online rolling code analyzer and generator)
It is an open-source hardware platform, which means that users can customize and extend its capabilities according to their needs. Since it has NRF24L01 module, it could be possible to extend its feature to jamming 2.4 GHz, which I haven’t seen being done for this device.
Hardware Modules
The Evil Crow RF V2 is built with several key hardware components:
- ESP32 Microcontroller: This is the brain of the device, providing processing power and connectivity options, including Wi-Fi.
- CC1101 RF Modules: These modules handle the transmission and reception of RF signals. They support a wide range of frequencies. The dual CC1101 modules allow the device to operate on two different frequencies simultaneously, increasing its flexibility with removable antennas.
- NRF24L01 Module: Used for specific types of RF attacks, such as mousejacking. This module operates in the 2.4GHz band and is commonly used for wireless communication in various applications.
- SD Card Slot: Allows for storage of captured signals and other data. This feature is particularly useful for logging and analyzing RF signals over extended periods. It also hosts local web panel.
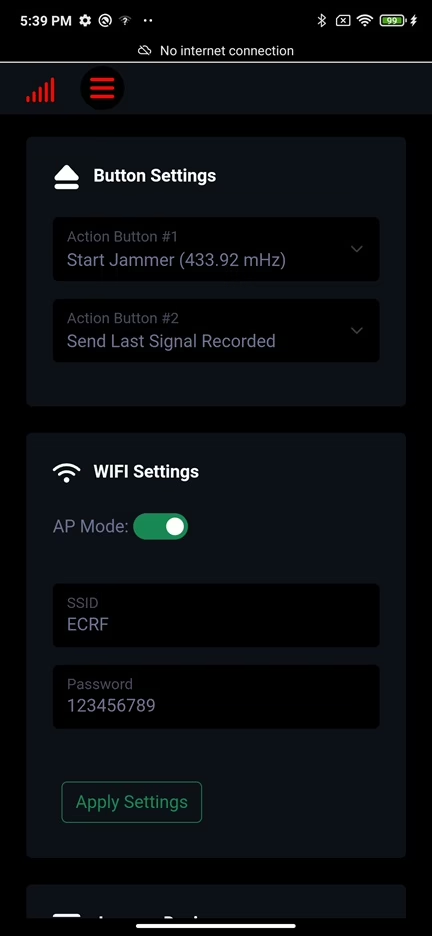
Additionally, the device relies on power source. There are two options how to power, it either using a LiPo battery through built-in connector or an external source via USB. Evil Crow RF V2 has three hardware buttons, where two of them can be customized to perform specific, user assigned functions, such as replay the last received signal or transmit any custom frequency.

Similar Products
Several other devices offer similar functionalities to the Evil Crow RF V2:
- Flipper Zero: A multi-tool that supports the same sub-GHz range of frequencies and protocols, making it a strong competitor. The Flipper Zero is known for its extensive feature set, including NFC, RFID, and infrared capabilities. However, it comes at a higher price point and may not be available in all regions. On the other hand, the active community, dedicated developers, and custom firmware create an excellent environment for future projects and ongoing support.
- Yard Stick One: A sub-GHz wireless transceiver that is popular for its ease of use and extensive community support. The Yard Stick One is designed for low-power, long-range communication and is widely used in IoT applications. It also comes with a higher price and having only one radio module.
- PandwaRF Marauder Basic: A sub-GHz tool that can operate autonomously, capturing and storing RF data without needing a smartphone connection. Unfortunately, I don’t have it to compare all of its features. Price tag is around $700 USD.
- SDR: A software-defined radio (SDR) that covers a broad frequency range from 1 MHz to 6 GHz, not just below 1GHz. This is a different league. Most popular SDRs are HackRF, LimeSDR, RTL-SDR, BladeRF etc. It is highly flexible and is used in a variety of applications, from signal analysis to protocol development. It isn’t correct to compare these with sub-GHz, however it is necessary to be aware of them.
Compared to these devices, the Evil Crow RF V2 stands out for its portability and ease of use. However, the Flipper Zero offers more features and a larger community, albeit at a higher price point and limited availability in some regions.
To be clear Evil Crow RF is not a Software-Defined Radio (SDR). It is a dual-radio RF tool. It operates with two CC1101 transceivers, allowing it to transmit and receive in multiple frequency ranges (300–348 MHz, 387–464 MHz, and 779–928 MHz).
Unlike an SDR, which can receive and transmit a wide range of frequencies and demodulate signals in software, the Evil Crow RF V2 is limited to the frequencies supported by the CC1101 chips and operates with predefined modulation schemes. However, it is highly effective for replay attacks, signal jamming, and other wireless security research applications.
Where to buy?
You can order it online from Sapsan Cybersec & Military store for around $67 USD with world-wide shipping.
Firmware Options
The Evil Crow RF V2 can run different firmware versions, each offering unique capabilities:
- Official Firmware: Developed by Joel Serna, this firmware supports basic functionalities such as signal transmission and reception, replay attacks, and mousejacking. The official firmware is designed to provide a solid foundation for RF hacking activities.
- Custom Firmware by h-RAT: This extended version includes interoperability with the Flipper Zero, allowing sub-GHz files to be interchangeable between the two devices. This firmware adds features like signal scanning, brute force attacks, rolljam attacks and others.
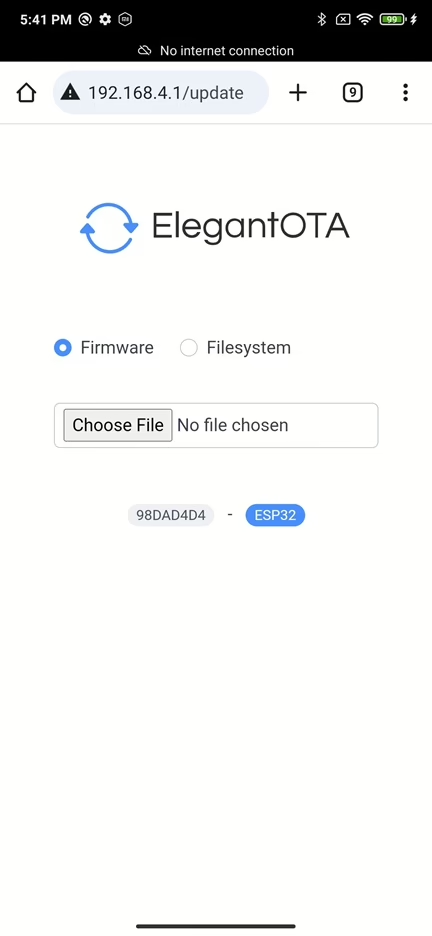
Firmware updates are conventionality done through web interface, by uploading firmware bin file.
In screenshot below is a visualization of receiving a signal from Record menu.
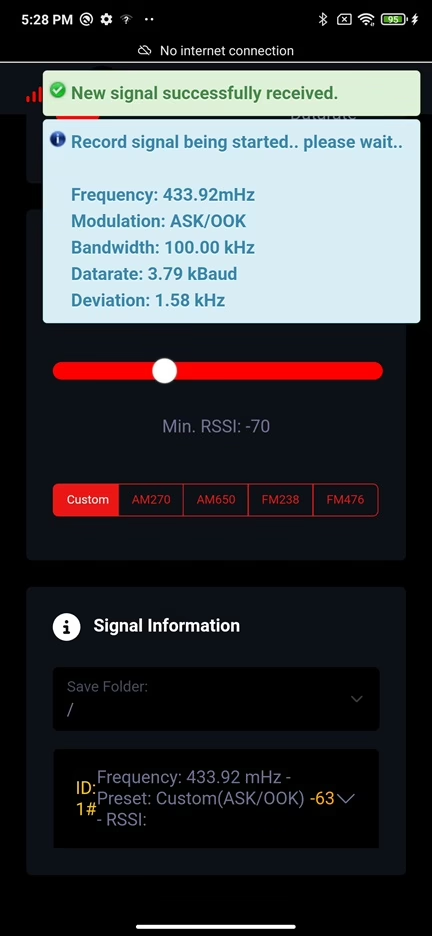
Received data are displayed in the bottom of the website and stored temporarily. By opening a ID of received signal (ID 1#), you can replay it, analyze it using Kaiju (don’t forget to enter API key in settings) or save it on micro SD card.
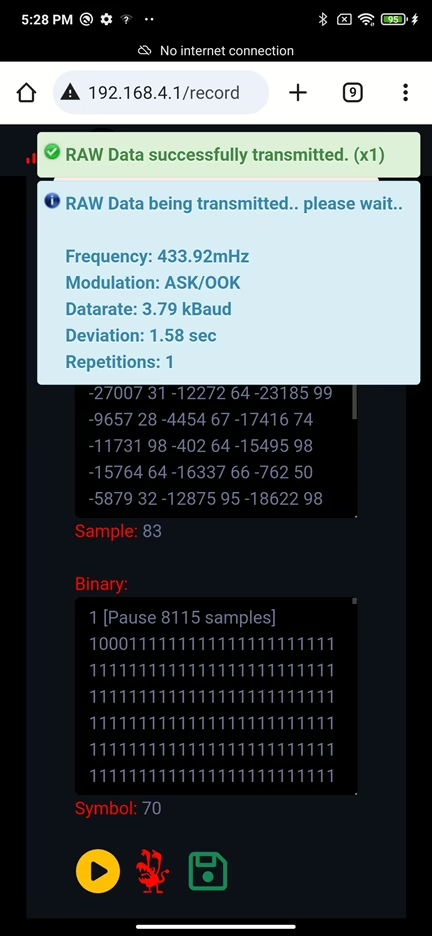
I have tested only this two firmware, where custom one created by h-RAT is more suitable by having more features. Both firmware versions create an access point for connection and operation, making it easy to control the device via a smartphone, or computer.
Custom 3D Cases
For those who like to beautify their gadgets, there are several 3D-printable cases available for the Evil Crow RF V2. Other can be found on platforms like Thingiverse and Yeggi. They offer additional protection and can make room for battery. Custom cases can improve the device’s portability. I have printed for myself Variant 1, it fits nicely.

Portability
One of the biggest advantages of the Evil Crow RF V2 is its portability when used with a smartphone. Unlike some RF tools that require bulky external batteries, the Evil Crow RF V2 can be powered directly from a mobile device, making it convenient for on-the-go use. Simply connect it to your smartphone using an OTG adapter, and then access its interface by connecting to the Wi-Fi access point it broadcasts.

This setup eliminates the need for a laptop, or serial communication, allowing you to perform tests discreetly just with your phone. Even with a 3D-printed case, the device remains compact and easy to carry, making it blend seamlessly into your pocket or bag without drawing unwanted attention.

Conclusion
While the Evil Crow RF V2 is a fantastic portable sub-GHz hacking tool, there are alternatives like the Flipper Zero that offer similar functionalities with added features. However, the Flipper Zero comes at a higher price and may not be available in all countries. On top of that, to cover the same range as Evil Crow, Flipper Zero would need an additional external CC1101 module. If you want to follow rabbit hole of radio frequencies, then you should go for SDR with wider spectrum, not just under 1GHz. Also make sure to buy SDR that can transmit signal, not only receive, such as RTL-SRD.
In conclusion, the Evil Crow RF V2 is an excellent choice for cybersecurity enthusiasts looking for a portable, smartphone-operated RF hacking device. Its compact size, versatile capabilities, and ease of use make it a valuable addition to any pentester’s toolkit. Firmware is open-source and was already customized that makes controlling Evil Crow very convenient. The fact that it can transmit and replay Flipper Zero created .sub files makes it very useful. The Evil Crow RF V2 offers a practical and affordable solution for RF hacking on the go.


I want to buy this make sure to selling in india also plz try to send up in india
I’m not that much of a online reader to be honest but your sites really
nice, keep it up! I’ll go ahead and bookmark your website
to come back in the future. All the best
How to purchase, for my wireless penetration testing activity as i am professional pen tester
Costo lo vendi?