![]()
Being automatically reconnected to known Wi-Fi networks is a convenience that comes with security risks, one of them being the Wi-Fi Karma Attack. Cybercriminals can use this method to trick unsuspecting users into automatically connecting to rogue Wi-Fi networks, potentially exposing privacy information by revealing access points where they were connected in the past, lure credentials or allow victim to download malicious app using captive portal.
In this article, we’ll explore what a Wi-Fi Karma attack is, how it works, how cybercriminals can use it maliciously using mobile devices, and most importantly, how to protect yourself.
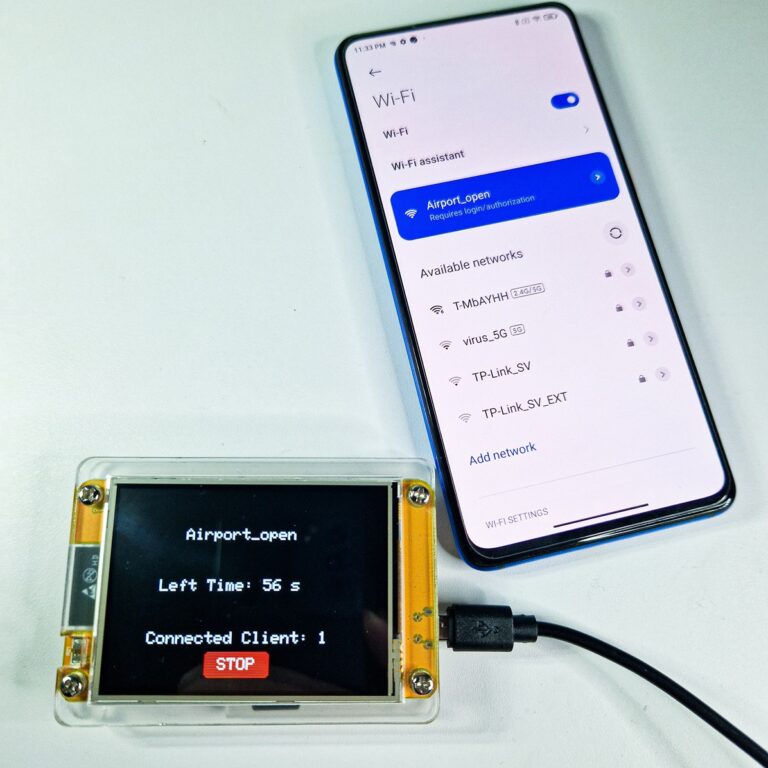
In the demonstration below I used Cheap Yellow Display device running Evil-M5Project firmware to make targeted device automatically connect to my device and display custom captive portal web. Connection happens without user interaction, however, user needs to click on the request to authorize to network.
Disclaimer: This article is for educational purposes only. The intent is to raise awareness about Wi-Fi Karma attacks and help users protect themselves. Unauthorized access to networks or devices is illegal and unethical.
What is a Wi-Fi Karma Attack?
A Wi-Fi Karma attack exploits the way devices search for previously connected Wi-Fi networks. Modern smartphones, laptops, and tablets are designed to remember trusted networks and automatically reconnect to them for user convenience. This behavior can be leverage to create rogue Wi-Fi networks that mimic trusted ones, tricking devices into connecting without user intervention.
Once a device connects, attackers can intercept unencrypted communications (such as HTTP, FTP but not HTTPS), steal credentials, or offer to download and install malicious apps.
How Does a Wi-Fi Probe Request Work?
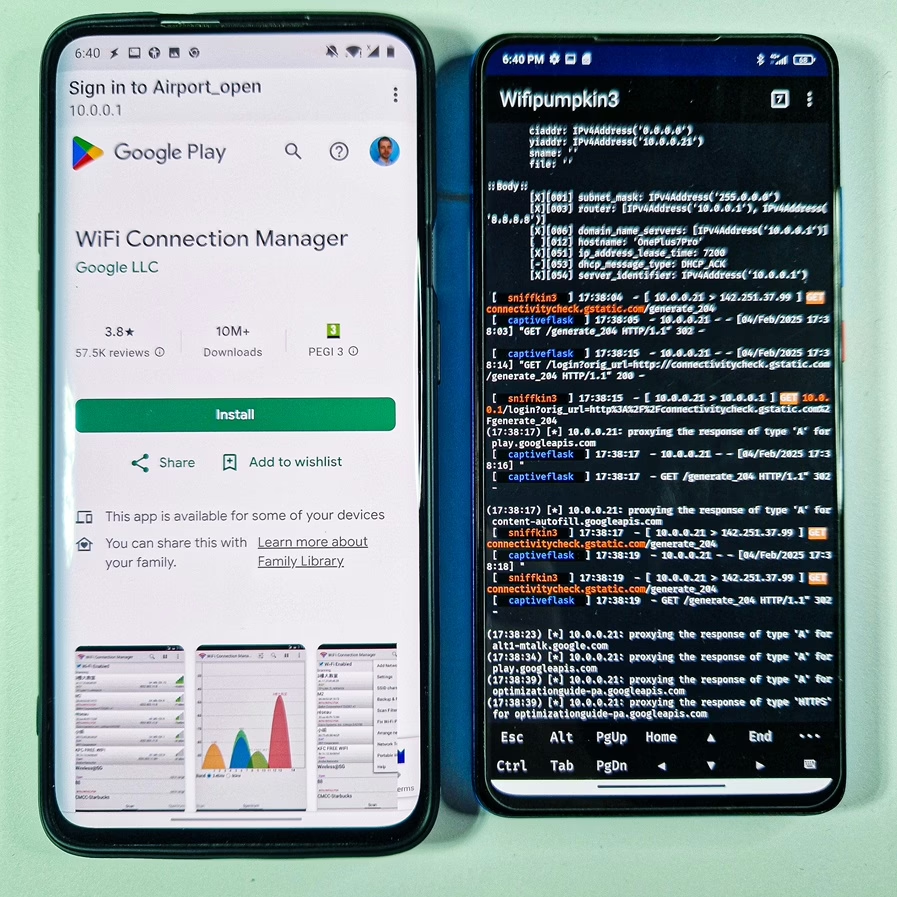
To understand Wi-Fi Karma attacks, it’s crucial to grasp how Wi-Fi probe requests function. When a device’s Wi-Fi is enabled, it constantly scans for available networks by sending out probe requests. These requests contain the SSIDs (network names) of some of previously connected networks. If a nearby Wi-Fi access point (AP) recognizes the SSID, it responds, and the device attempts to connect.
However, attackers take advantage of this behavior by using specialized tools to capture probe requests and set up a rogue access point that falsely claims to be the requested network. This tricks the device into connecting automatically, thinking it’s a legitimate network.
Which Networks Broadcast Probe Requests?
Only networks with hidden SSIDs require devices to send probe requests explicitly asking for them. This is because a hidden SSID does not broadcast its presence in beacon frames like normal networks. Instead, a device that has previously connected to a hidden SSID will actively probe for it by sending out its name in a request. This behavior makes hidden SSIDs less secure than commonly believed, as attackers can easily capture these probe requests and determine the SSID, allowing them to set up a rogue access point mimicking the hidden network. This is a reason why hidden networks are not truly hidden.
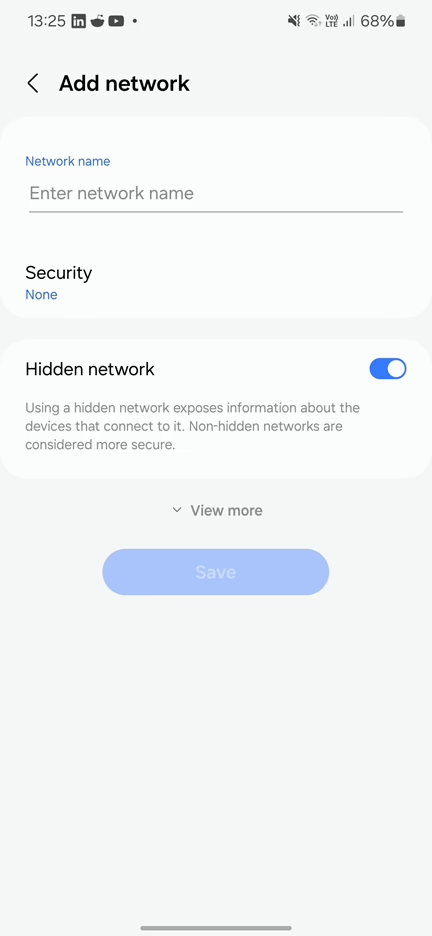
If a user manually attempts to connect to a hidden network with open security (via the ‘Add network‘ option in Wi-Fi settings) and mistakenly enters an incorrect network name, the device will not establish a connection. However, the device will continue broadcasting the entered SSID in subsequent probe requests. This also applies for physical security, where anyone with access to your device could manually add this network and later on spoof it to make you connect and lure sensitive information. Of course, this scenario is very limited.
Encryption Type is Not Visible in Probe Requests
When a device sends out probe requests, it only broadcasts the SSID (network name) of previously connected networks. However, these requests do not include information about the encryption type (such as WPA2, WPA3, or Open). This means that an attacker cannot determine whether a network is secured or not just from the probe request alone. As a result, the only viable targets for a Karma attack are open (unencrypted) networks, where a device will automatically connect without requiring authentication.
A Network That Doesn’t Broadcast Can Still Auto-Reconnect
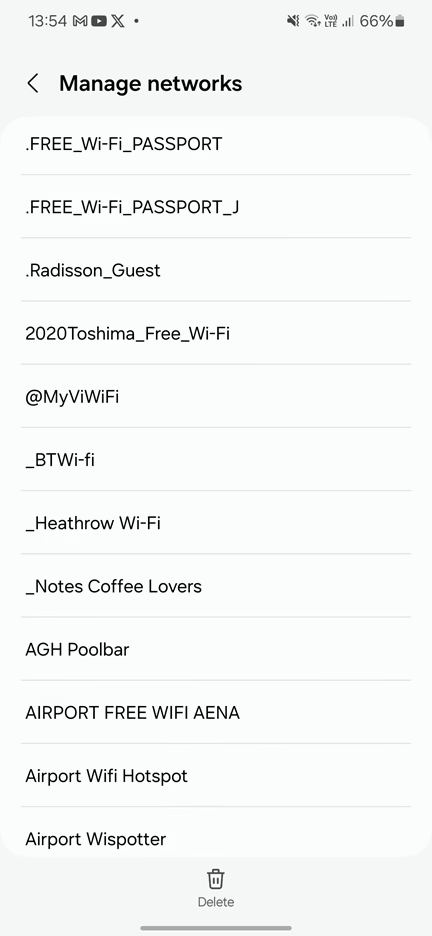
Even when a device is not broadcasting probe requests for hidden networks, it can still automatically reconnect to Wi-Fi networks it has connected to in the past. This is particularly relevant for networks with open security. The list of such networks is stored in the Wi-Fi settings under “Manage Networks.”
If a threat actor creates a rogue access point with the same name as one of these previously connected networks, the smartphone will, by default, automatically connect to it.
However, for a threat actor to exploit this, they would need to know the names of the networks stored on the target device. Without physical or remote access to the device, obtaining this list is not possible. Therefore, threat actors often resort to guessing common network names such as “free wifi,” “airport hotspot,” or “guest.” To lists most popular open networks in the area can be use OSINT tool Wigle. They may also conduct reconnaissance to identify networks that the target is likely to have used, such as those at frequently visited coffee shops, airports, train stations, and other public places.
Can a Device Be Targeted While Connected to Another Network?
Yes, a device can still fall victim to a Karma attack even if it is already connected to another Wi-Fi network. Attackers can achieve this by performing a deauthentication attack on the current network. This forces the victim’s device to disconnect, making it search for known networks. The attacker then immediately starts the Karma attack by impersonating a trusted SSID, tricking the device into reconnecting to the rogue access point.
Attackers Can Use Smartphones for Stealthy Execution
Traditionally, Wi-Fi Karma attacks required a laptop with a supported wireless network adapter capable of packet injection. However, an attacker can now execute these attacks using a customized smartphone. Certain Android devices with modified software and tools such as Kali NetHunter allow attackers to create rogue networks and exploit victims on the go. This makes the attack highly stealthy and portable, as a cybercriminal can blend in among everyday users without drawing attention. A Wi-Fi Karma attack enhances traditional rogue access point attacks by responding dynamically to probe requests. Instead of setting up a specific SSID, an attacker’s system automatically impersonates any network that a nearby device is searching for. In the Figure 4, you can see airodump-ng tools scanning for Wi-Fi devices in vicinity, and receiving probe requests from devices.
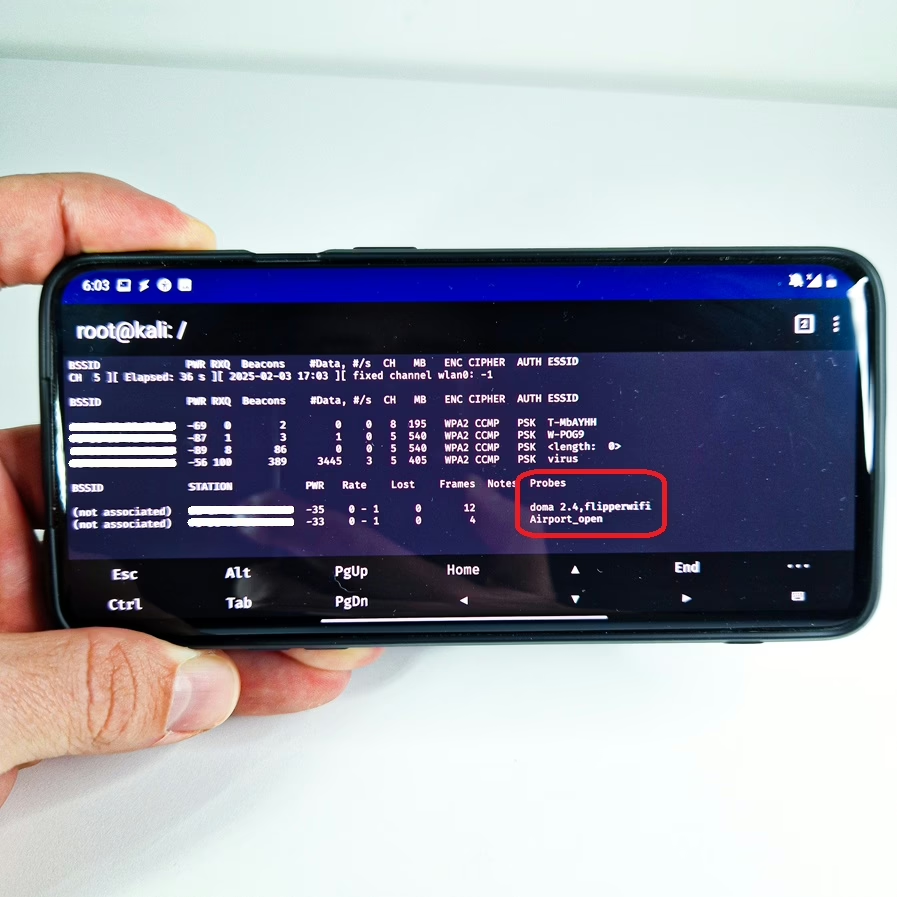
Karma Attack and Captive portals
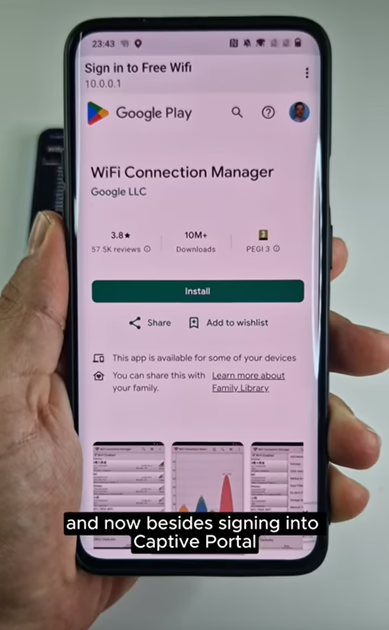
To be Karma attack can be combined with other deceptive techniques for greater effectiveness. One common enhancement is captive portal. A captive portal is a web page that users must interact with before accessing a network. Commonly found in public Wi-Fi hotspots like cafes, hotels, and airports, captive portals often require users to accept terms, enter credentials, or log in via social media. While legitimate businesses use them for authentication and user tracking, attackers can exploit captive portals to harvest credentials or distribute malware.
- Device Probe Requests: A victim’s device sends out probe requests asking for known networks. These requests are sent for preferred networks and for hidden SSIDs.
- Attacker’s Rogue AP Listens: The attacker’s malicious access point (AP) captures the requests.
- Impersonation: The rogue AP spoofs the SSID of the requested network and fooling the victim’s device into automatically connecting.
- Unaware Connection: The victim’s device connects to the fake network, believing it’s a trusted one.
- Exploitation: The attacker can now perform various malicious activities, credential harvesting via custom captive portal, or advises to download malware impersonating legitimate app.
Prevention
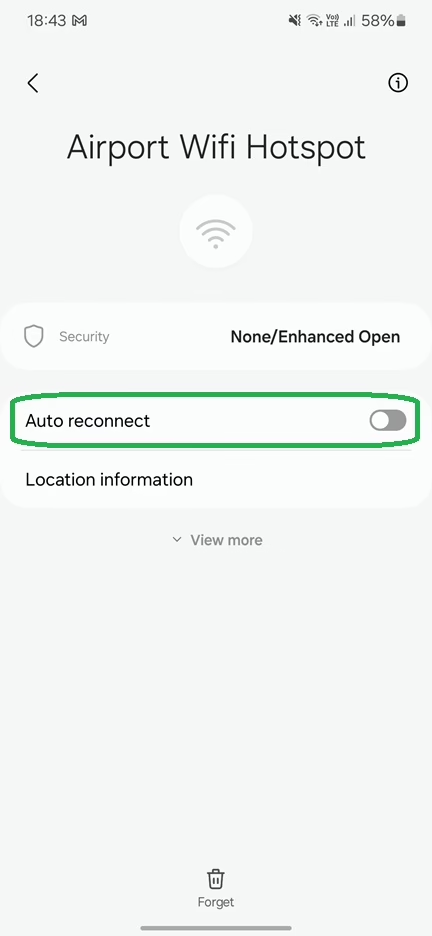
1. Disable Auto Reconnect to Wi-Fi Networks
Many devices have an auto-connect feature that joins known networks automatically. Disable this feature to ensure that you manually verify every Wi-Fi connection.
2. Forget Unused Wi-Fi Networks
Manually forget public and open networks from your device settings. This limits the number of probe requests sent, making it harder for attackers to exploit.
3. Turn Off Wi-Fi When Not in Use
If you are not actively using Wi-Fi, disable it. This prevents your device from broadcasting probe requests and reduces exposure to potential attacks.
4. Use Cellular Data Instead of Public Wi-Fi
Whenever possible, use your mobile data connection instead of untrusted public Wi-Fi, especially when accessing sensitive accounts or conducting transactions.
5. Verify Captive Portals
Before entering credentials into a captive portal, confirm with staff or check signage for the correct Wi-Fi network name and login page.
Conclusion
Always be cautious when connecting to public Wi-Fi, and prioritize security over convenience. Awareness and vigilance are your best defenses against cyber threats. Wi-Fi Karma attacks are a significant threat that exploits how devices remember and reconnect to networks. By impersonating trusted Wi-Fi networks, attackers can try to lure credentials, and even install malware. With the advent of mobile technology, attackers no longer require bulky hardware—customized smartphones or mobile gadgets such as Cheap Yellow Display can now be used to perform these attacks stealthily. However, by understanding the risks and taking proper precautions—such as disabling auto-connect and verifying Wi-Fi networks—you can greatly reduce the likelihood of falling victim to such attacks.