![]()
The M5StickC Plus 2 is a compact, ESP32-based development board with built-in Wi-Fi, infrared and Bluetooth capabilities. When paired with the Nemo firmware, developed by 4x0nn, it becomes a powerful tool for high-tech pranks, wireless attacks, and creative experiments. Many times, it is compared to Flipper Zero, however it has less possibilities. In this blog, we will delve into the features of the M5StickC Plus 2 running Nemo firmware and focus on one of its features – the Wi-Fi Evil Portal Attack. I will delve into this topic because of recent news were man was charged over creation of ‘evil twin’ free Wi-Fi networks to access personal data on airplane. For some reason, my first thought was that it is easily possible using M5Stick, since most likely it is the smallest device with built-in display, Wi-Fi and battery that can start evil twin attack from a palm of a hand.
Features of Nemo Firmware
- TV-B-Gone: Ever wanted to turn off any infrared-controlled TV or projector? NEMO’s got you covered. This feature you could most likely see being used by Flipper Zero. Activate the TV-B-Gone feature, and watch screens go dark at your command.
- AppleJuice/BadBT: This feature spams iOS devices with Bluetooth advertisements.
- Wi-Fi Spam: NEMO lets you create funny or random SSIDs for Wi-Fi networks.
- Evil Portal: It’s an evil captive portal that tries to social engineer email credentials. It can clone and even deauthenticate already discovered network.
- Wi-Fi deauthentication: Disconnect devices from selected network.
- SSID Scanner: Discover nearby 2.4 GHz SSIDs, get info about them.
- QR Codes: Can generate customized QR codes. However, it’s necessary to write them in source code, built it and flash it.
- 24-Hour Digital Clock: A user-adjustable clock backed by the M5Stick RTC. It keeps relatively stable time even during deep sleep and low battery mode.
Evil Portal Attack
One of the most potent features of the M5StickC Plus 2 running Nemo firmware is the ability to carry out a WiFi Evil Portal Attack. This attack involves creating a fake WiFi network and capturing the credentials of the victims who connect to it. The attacker deauthenticates a user connected to a legitimate internet access point, then creates a rogue access point looking similar to the legitimate internet access point. The victim unknowingly connects to the rogue access point. From the rogue access point, the attacker is able to launch phishing attacks. This attack is also possible to carry using and Android smartphone running NetHunter.
Identify Fake Wi-Fi Access Points
With technical skills, theoretically you can identify Evil Twin access points using a Snappy tool. You can use airodump-ng to create pcap before and after suspicions access point appears. Then use Snappy tool to compare their outputs with networks fingerprints. If their hash is not equal, it might be a fake access point.
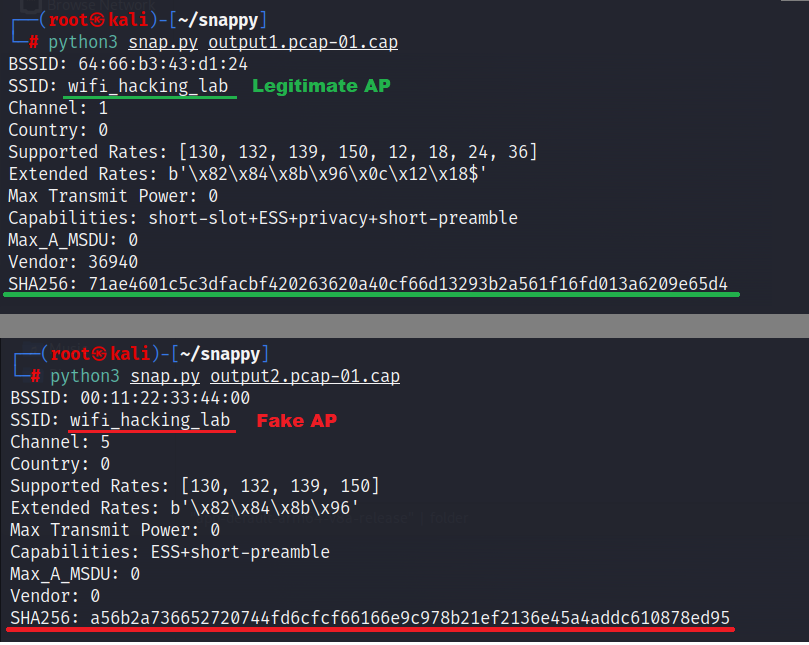
If you are interested, you can also check recently published paper about detection and mitigation of MITM attacks with evil access points.
Prevention against Evil Twin Attacks using Captive Portals
- Avoid Unsecured Wi-Fi Networks: If a network appears unsecure, steer clear. Evil twin networks often masquerade as unsecured hotspots.
- Two-Factor Authentication (2FA): Enable 2FA wherever possible to add an extra layer of security.
- Personal Hotspot: Whenever possible, use your own personal hotspot instead of public Wi-Fi.
Conclusion
The M5StickC Plus 2 running Nemo firmware is a powerful tool with a wide range of features. While these features can be used for harmless pranks and network scanning, they can also be used maliciously in the wrong hands. Therefore, it’s crucial to understand not only how to use these features but also how to protect yourself from potential attacks.

