![]()
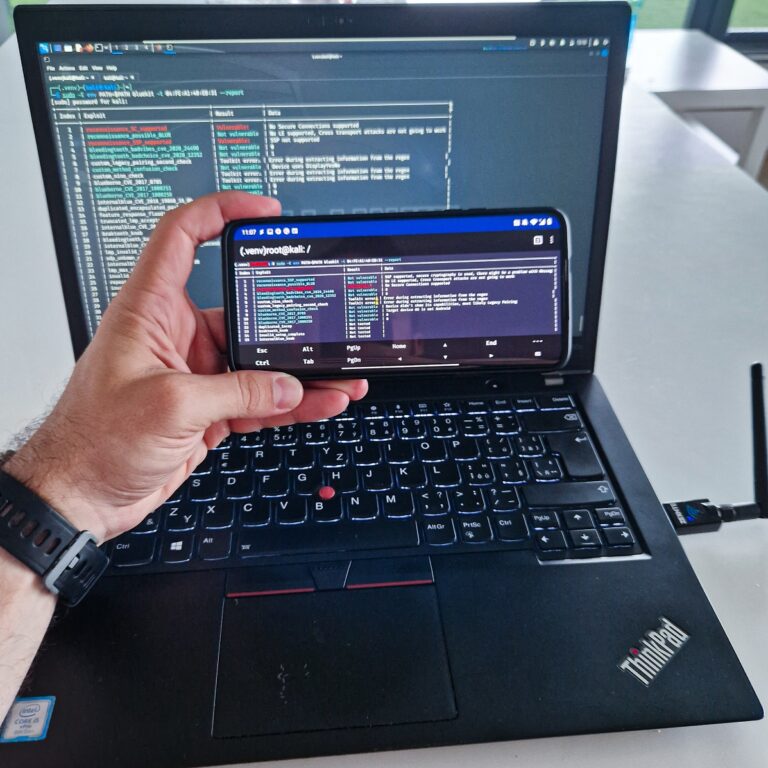
BlueToolkit is an extensible Bluetooth Classic vulnerability automated testing framework. It’s designed to uncover both new and old vulnerabilities in Bluetooth-enabled devices. Moreover, since it runs on Linux based devices, it is possible to install it on rooted Android smartphone and make it a portable and automated Bluetooth vulnerability scanner. This makes it a capable tool for vulnerability research, penetration testing, and Bluetooth hacking.
How Does BlueToolkit Work?
BlueToolkit operates by executing templated exploits one by one against the targeted device. Based on documentation it can test up to 43 Bluetooth exploits and even allows to add new one. To test some of them, it is necessary to have hardware that is listed below. However, after running and listing available exploits while executing the tool, I was presented with information that its able to test 11 vulnerabilities without additional hardware, out of 39, see Figures below.
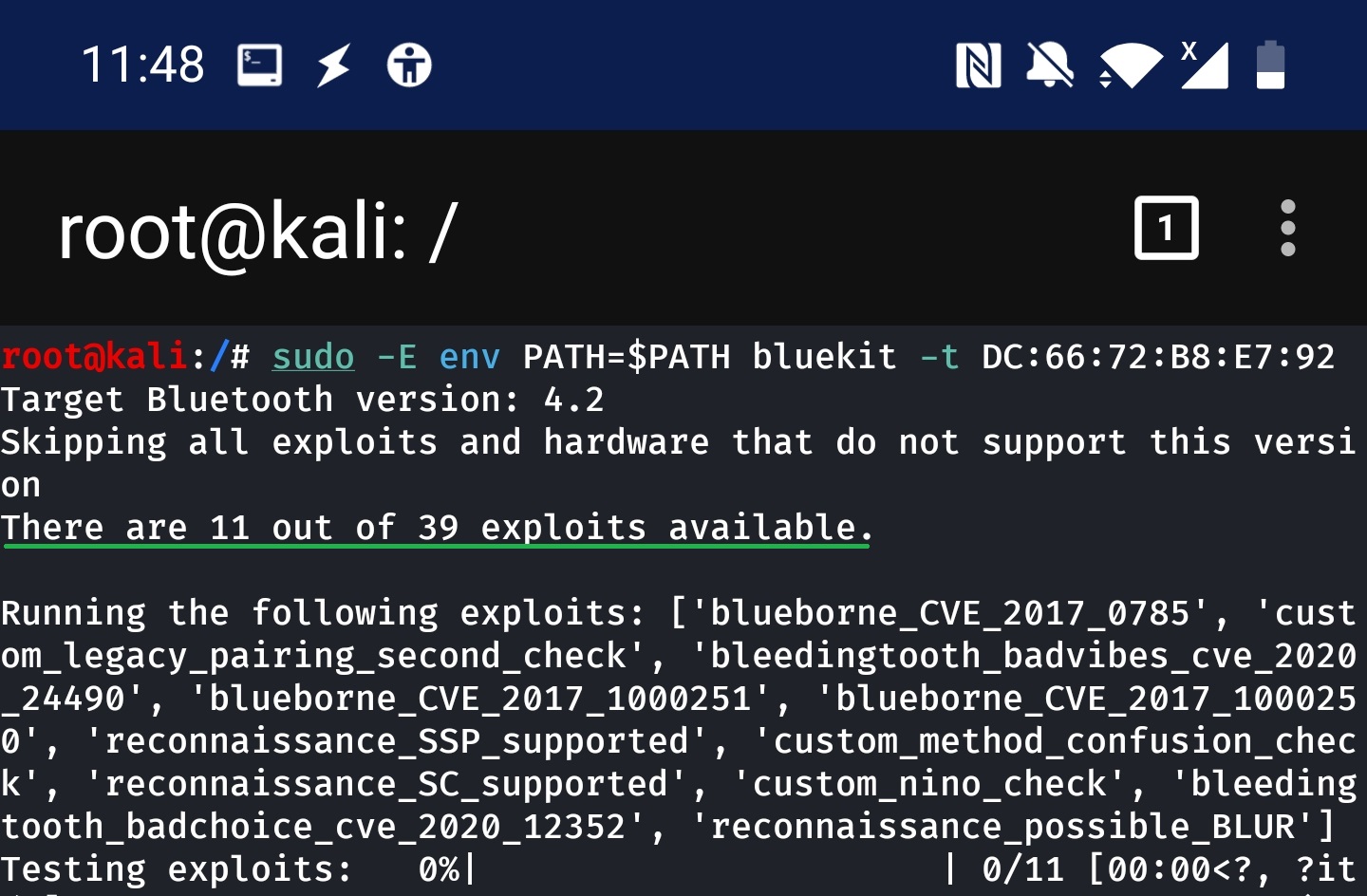
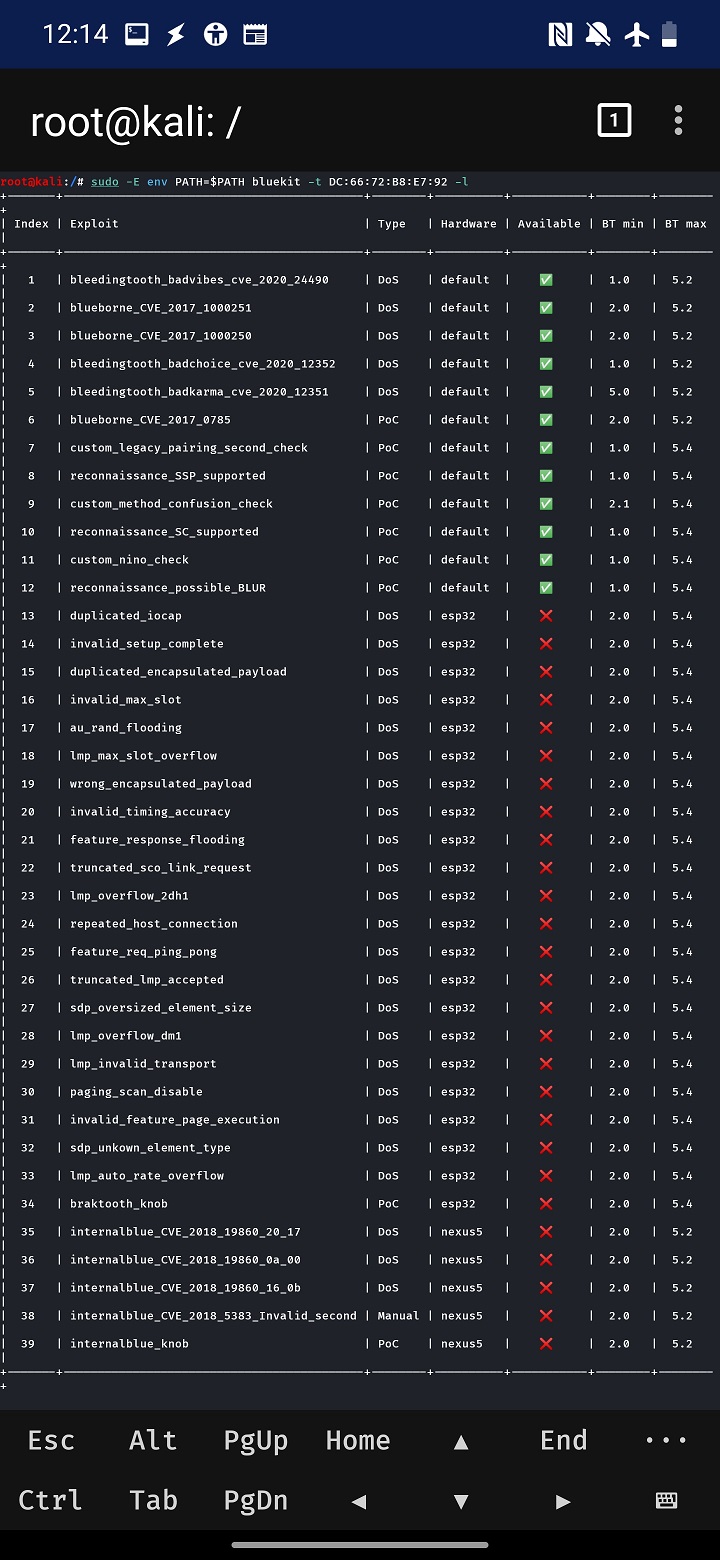
To test some of the vulnerabilities additional hardware is required, such as
- ESP-WROVER-KIT-VE for Braktooth,
- Nexus 5 for Internal blue-based vulnerabilities,
- CYW920819M2EVB-01 for BIAS, BLUR and BLUFFS attacks.
Installation and usage
BlueToolkit runs only on Linux, installation guide you can follow on the GitHub. This means that you can also run it while on the go on Android smartphone. The Android needs to be rooted, with kernel drives support for a Bluetooth chip or an external adapter. So, if you have already setup your NetHunter, then you should be good to go. I was also able to run it on Kali Linux in a Virtual Machine using an external Bluetooth adapter, particularly Zexmte. Specific commands and their usage are very well explained in a Workflow section. Results of my scan while I was inspecting a Bluetooth speaker are visible below.
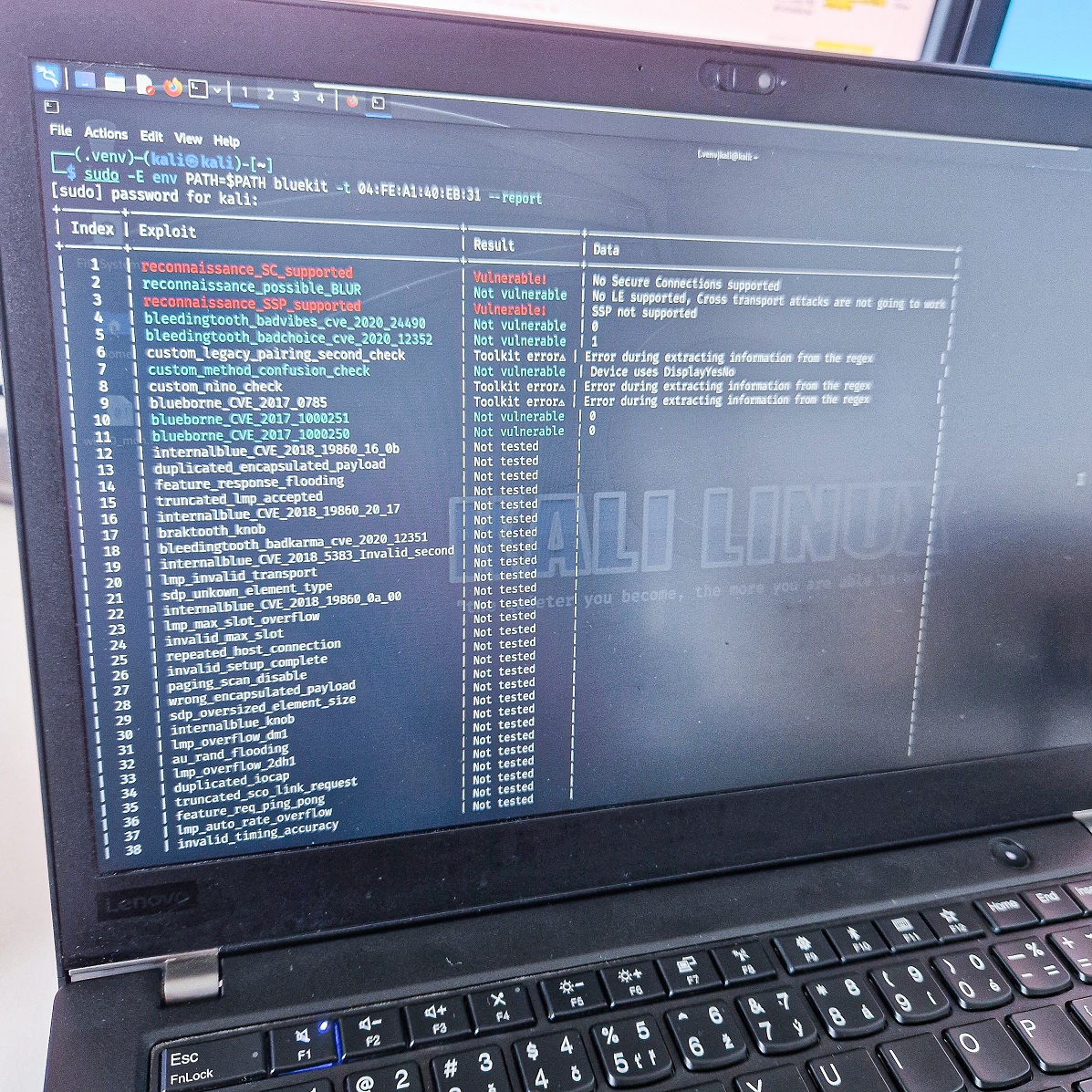
Tested vulnerabilities
A list of tested vulnerabilities and attacks based on the documentation is visible below.
| Vulnerability | Category | Type | Verification type | Hardware req. | Tested |
| Always pairable | Chaining | Chaining | Manual | ✓ | |
| Only vehicle can initiate a connection | Chaining | Chaining | Manual | ✓ | |
| Fast reboot | Chaining | Chaining | Manual | ✓ | |
| SC not supported | Chaining | Info | Automated | ✓ | |
| possible check for BLUR | Chaining | Info | Automated | ✓ | |
| My name is keyboard | Critical | RCE | Semi-automated | ✓ | |
| CVE-2017-0785 | Critical | Memory leak | Automated | ✓ | |
| CVE-2018-19860 | Critical | Memory execution | Automated | ✓ | |
| V13 Invalid Max Slot Type | DoS | DoS | Automated | ✓ | ✓ |
| V3 Duplicated IOCAP | DoS | DoS | Automated | ✓ | ✓ |
| NiNo check | MitM | MitM | Semi-automated | ✓ | |
| Legacy pairing used | MitM | MitM | Automated | ✓ | |
| KNOB | MitM | MiTM | Semi-automated | ✓ | ✓ |
| CVE-2018-5383 | MitM | MiTM | Automated | ✓ | ✓ |
| Method Confusion attack | MitM | MiTM | Automated | ✓ | |
| SSP supported <= 4.0 weak crypto or SSP at all | MitM | Info/MitM | Automated | ✓ | |
| CVE-2020-24490 | Critical | DoS | Automated | ✓ | |
| CVE-2017-1000250 | Critical | Info leak | Automated | ✓ | |
| CVE-2020-12351 | Critical | RCE/DoS | Automated | ✓ | |
| CVE-2017-1000251 | Critical | RCE/DoS | Automated | ✓ | |
| V1 Feature Pages Execution | Critical | RCE/DoS | Automated | ✓ | ✓ |
| Unknown duplicated encapsulated payload | DoS | DoS | Automated | ✓ | ✓ |
| V2 Truncated SCO Link Request | DoS | DoS | Automated | ✓ | ✓ |
| V4 Feature Resp. Flooding | DoS | DoS | Automated | ✓ | ✓ |
| V5 LMP Auto Rate Overflow | DoS | DoS | Automated | ✓ | ✓ |
| V6 LMP 2-DH1 Overflow | DoS | DoS | Automated | ✓ | ✓ |
| V7 LMP DM1 Overflow | DoS | DoS | Automated | ✓ | ✓ |
| V8 Truncated LMP Accepted | DoS | DoS | Automated | ✓ | ✓ |
| V9 Invalid Setup Complete | DoS | DoS | Automated | ✓ | ✓ |
| V10 Host Conn. Flooding | DoS | DoS | Automated | ✓ | ✓ |
| V11 Same Host Connection | DoS | DoS | Automated | ✓ | ✓ |
| V12 AU Rand Flooding | DoS | DoS | Automated | ✓ | ✓ |
| V14 Max Slot Length Overflow | DoS | DoS | Automated | ✓ | ✓ |
| V15 Invalid Timing Accuracy | DoS | DoS | Automated | ✓ | ✓ |
| V16 Paging Scan Deadlock | DoS | DoS | Automated | ✓ | ✓ |
| Unknown wrong encapsulated payload | DoS | DoS | Automated | ✓ | ✓ |
| Unknown sdp unknown element type | DoS | DoS | Automated | ✓ | ✓ |
| Unknown sdp oversized element size | DoS | DoS | Automated | ✓ | ✓ |
| Unknown feature req ping pong | DoS | DoS | Automated | ✓ | ✓ |
| Unknown lmp invalid transport | DoS | DoS | Automated | ✓ | ✓ |
| CVE-2020-12352 | Critical | Info leak | Automated | ✓ |
Real-World Impact
BlueToolkit has already discovered 64 new vulnerabilities across 22 products, which means that it might help other researchers to identify security issues in Bluetooth. Details about these vulnerabilities as well as affected devices will be published in August 2024 most likely on their GitHub page.
Conclusion
In conclusion, BlueToolkit is a powerful tool for anyone interested in Bluetooth security. Based on the results of its usage, it seem to be a valuable asset for any wireless security researcher or penetration tester.