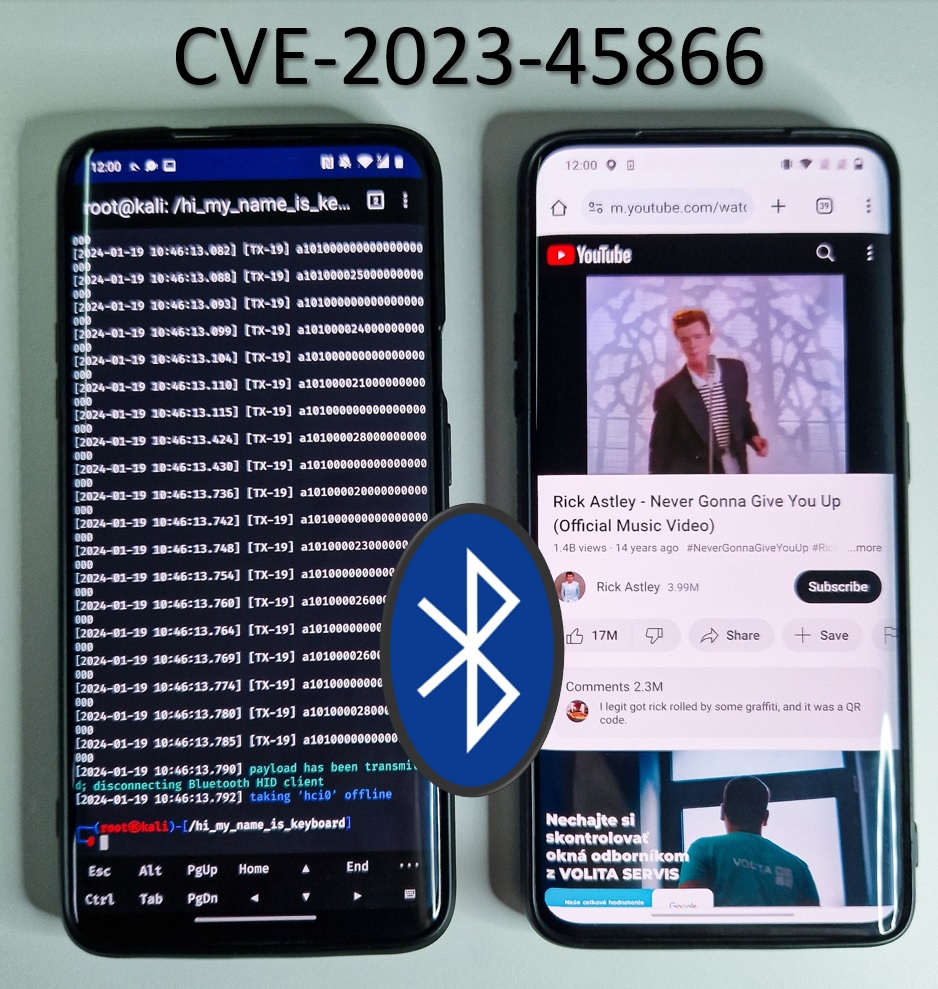
Exploiting 0-click Android Bluetooth vulnerability to inject keystrokes without pairing
[update 2024-02-19] This vulnerability can be even used to remotely wipe data of targeted Android smartphone. Using this vulnerability it is possible to guess user lock screen PIN. After five incorrect PINs device is locked out for 30 seconds. This operation results in locking user out of its device in a loop. If Auto factory … Continue reading Exploiting 0-click Android Bluetooth vulnerability to inject keystrokes without pairing
11 Comments