![]()
The Kitchen Sink is a name of Bluetooth Low Energy (BLE) attack that sends random advertisement packets that targets iOS, Android, and Windows devices the same time in the vicinity. The attack is called “Kitchen Sink” because it tries to send every possible packet in the list, similar to the phrase “everything but the kitchen sink”. So far, we could run the Kitchen Sink only by using Flipper Zero device, as I explained and demonstrated in my previous blog. However, not everyone has a Flipper Zero and since we are mobile people, we need mobile apps. Thanks to Simon, we can use Kitchen Sink in a standalone Android Bluetooth LE Spam application that you can download from his GitHub. As default Android system prevention against these Fast Paring messages, Android uses a model where the same device can send only few paring (around five) notifications in a row, and then it will be automatically ignored by the system. Using Kitchen Sink, I was able to send around 30 pop-ups in the row to Samsung FE20 running Android 13.
The app, besides “all-in-one” BLE spam, provides option to send BLE pairing messages separately to each operating system as well, see Figure 1.
List of notifications
Using Kitchen Sink, Bluetooth BLE Spam app can advertise all together up to 219 different devices. For those who are interested, here is the list.
Twelve Apple Device Popups:
- AppleTV Setup
- AppleTV Pair
- AppleTV New User
- AppleTV AppleID Setup
- AppleTV Wireless Audio Sync
- AppleTV Homekit Setup
- AppleTV Keyboard
- AppleTV ‘Connecting to Network’
- Homepod Setup
- Setup New Phone
- Transfer Number to New Phone
- TV Color Balance
Seventeen Apple Action Modals:
- Airpods
- Airpods Pro
- Airpods Max
- Airpods Gen 2
- Airpods Gen 3
- Airpods Pro Gen 2
- PowerBeats
- PowerBeats Pro
- Beats Solo Pro
- Beats Studio Buds
- Beats Flex
- BeatsX
- Beats Solo3
- Beats Studio3
- Beats Studio Pro
- Beats Fit Pro
- Beats Studio Buds+
180 Android Fast Pairing devices, list is available on Flipper Xtreme Firmware GitHub.
And ten Microsoft Swift Paring with name Device and a number from 1 to 10. This name of a device can be customized, comparing it to the previous names which can’t be changed.
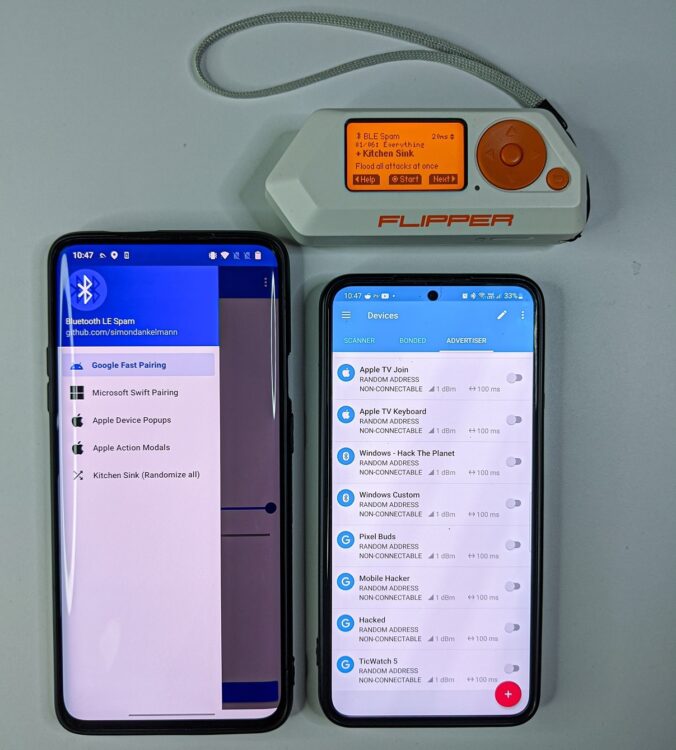
Comparing Flipper Zero with Bluetooth LE Spam and nRF Connect apps
At the time of writing this blog, if you are not having flashed dev build of Flipper Xtreme or Unleased firmware, then the Flipper has only list of five Fast Pairing Android devices, comparing to Bluetooth LE Spam app. However, this could be fixed by cloning BLE Spam branch from GitHub and build your own Flipper Zero app using flipc.
Disadvantage of the BLE Spam app comparing to Flipper Zero is the range it covers. Using Flipper Zero, I can send popups to each system from longer distance. Even though I set the signal (TX power) to the highest in Bluetooth LE Spam app, the range is still small. When I compared nRF Connect app with Bluetooth LE Spam, I got better results for nRF Connect. However, using nRF I tested only two proximity pairing messages for Pixel Buds and TicWatch 5. Below you can see the table with range comparison in meters (m). For clarification 1 meter is equal to around 3.28 US feet.
| Targeted OS/Device or app | Flipper Zero | Bluetooth LE Spam app | nRF Connect app |
| Android | over 15 m | 0.4 m | over 10 m |
| iOS | 50 m | 10 m (modals) | over 12 m (modals) |
| Windows | 0.5 m | 0.2 m | 0.2 m |
In the video below you can see the Kitchen Sink in action.
Conclusion
Based on my tests, the best area coverage has Flipper Zero, then nRF Connect and finally Bluetooth LE Spam app. I was really surprised by the nRF Connect signal strength. However, each of the apps has its benefits. Since, it is not possible to randomize proximity messages automatically using nRF Connect, to achieve the Kitchen Sink, only manually include them as advertisement packets and enable them all. Contrary, Bluetooth LE Spam app can automatize this task using the Kitchen Sink, but for some reason the range is lower than nRF Connect app. In the future, I can imagine that Bluetooth LE Spam app would come up with an option to manually pick one of the proximity messages and individually broadcast them which might as a result behave ask nRF Connect.
It is important to mention that spoofing Fast Pairing messages for Android using one device, such as Pixel Buds, is limited up to five times, then they are ignored by the Android system. However, using the Kitchen Sink, theoretically it is possible to spoof 180 devices. In my testes, I was able to spoof 30 devices in the row, then Android OS started to ignored them without any user interaction, which is a great anti BLE spam feature. There are no limits or restrictions enforced by iOS or Windows operating systems.

Nice nice nice! I’ve tried some days ago, watching you, thx
Thanks for coming back, hope it worked well 🙂
Hi! I’ve soome problem with Bluetooth LE Spam, it work fine only on a rooted mobile or every rooted and not?
By me, it’s show only 1 message spam and stop…
Same
Hello iam from India how can I get this blutooth aap for bluebug attack pls tell me can I Download it on my Android
Not work on my Android version 11
Weird. On my side, it works without any problem on Android 13, 11, and 10.
Good morning, can you post a screenshot or send me the exact setup data you entered into nrf connect to reach 10m with fast Pairing? If that’s possible i need to make it work in the Bluetooth-le-spam app 🤣
I checked your code and the Data and ServiceUuid are the same as – for example for Pixel Buds – as in mine nRF app. I guess there might be an issue with randomization. IMHO, if you would push Fast pair only for one particular device, you might achieve the same range as for nRF.
Thanks! i will definitely try that and investigate more 🙂
i tried the pixel buds with nrf this morning but only achieved about 40cm
Sorry, I forget to mention to also increase the transmitted power (TX) in Options of the advertising packet to 1 dBm and interval to 160ms.
Hi! Do you use Twitter? I’d like to follow you if that would be okay.
I’m absolutely enjoying your blog and look forward to new updates.
Hello, I am glad you find the content interesting. I have twitter, feel free to check it out: https://twitter.com/androidmalware2
Best regards
How to download
Please how to download
How can I install in android device?
I’m Italian and my English is non good
Thatnks
Hi all 🙂
just wanted to inform about the latest update (1.0.7), currently in pre-release state, the ios 17 crash is possible as well as colorized apple devices and the lovespouse adult toys you tweeted about. Even “denial of pleasure” is possible 😀
you can find the latest release here if you are interested:
https://github.com/simondankelmann/Bluetooth-LE-Spam/releases