![]()
Welcome to a next blog that focuses on NetHunter tools. In a previous post, I introduced the NetHunter apps that are preinstalled, and a few tools that are available in the NetHunter application. I hope that through this article, you will gain a deeper understanding of these tools and its capabilities, as well as learn some new tricks and techniques for your own penetration testing projects.
Today, we dive into three tools available in the NetHunter system: MAC changer, KeX Manager, and USB Arsenal. We will explore the features of MAC Changer, explain its importance in maintaining privacy during security testing, and provide step-by-step instructions on how to effectively change your MAC address using this tool. I will demonstrate how KeX Manager can significantly enhance your productivity and efficiency during mobile hacking and to understand USB Arsenal, since it will be a prerequisite for upcoming blog.
MAC Changer
MAC Changer in NetHunter is a graphic interface for macchanger utility that enables you to switch the Media Access Control (MAC) address of your device, which is a unique identifier assigned to every network device. This can be used to spoof the identity of the device, making it harder to track and monitor particular smartphone.
Android version 10 and above already provide MAC address randomization. The purpose of this app is then to manually generate or set a custom MAC address for the interface and change the device hostname.
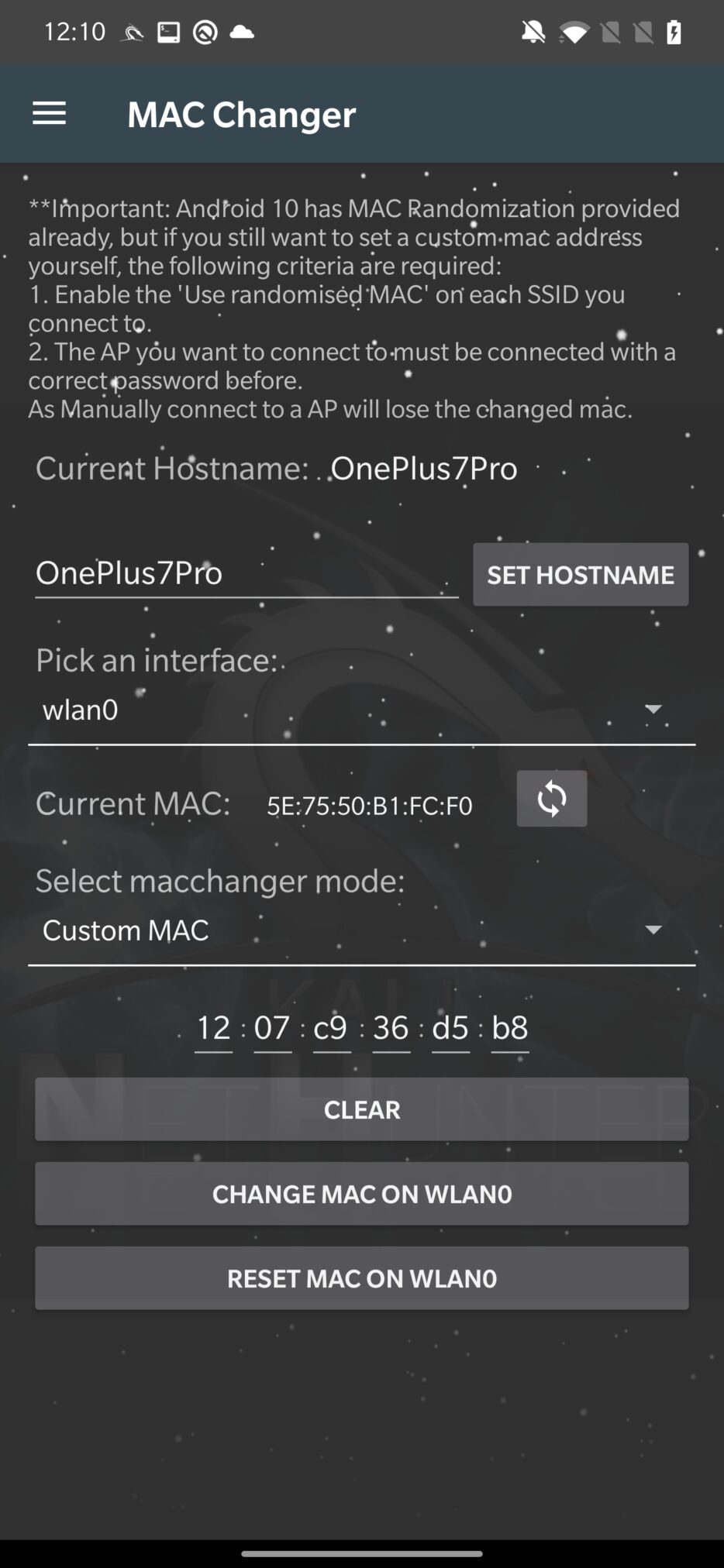
Changing the MAC address of your device can be useful in several situations, such as:
- Bypassing MAC filtering: Some networks may only allow devices with specific MAC addresses to connect, and changing the MAC address of your device can allow you to bypass this type of restriction.
- Anonymizing your device: Changing the MAC address of your device can help to obscure your identity on the network, making it more difficult for others to track your online activity.
KeX Manager
You can use the Kali Desktop Experience (KeX) feature on your Android device with the help of the KeX Manager tool. It’s a feature that lets you use a graphical desktop environment on your Android device, much like you would on a desktop computer.
You can change several KeX parameters, including the resolution and color depth of the desktop, as well as start or stop the KeX service using the KeX Manager.
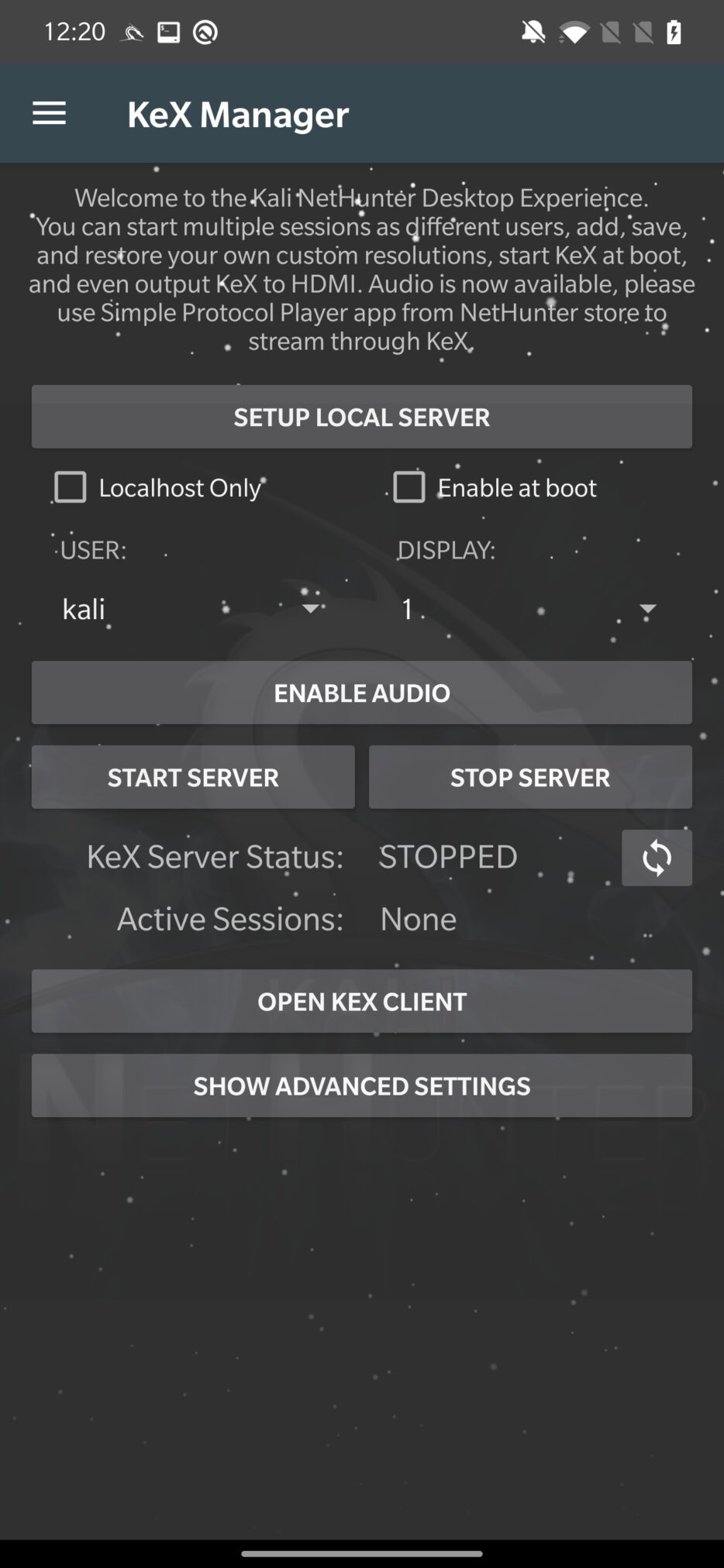
As was already explained in the post about installation of rootless Kali NetHunter, first you need to SETUP LOCAL SERVER, by setting a password to access the server. Choose either kali or root user, or create a new one. Then you need to START SERVER and OPEN KEX CLIENT. From client app, you need to enter only the VNC password, you just set and tap on Connect to create a desktop session as you can see in Figure 3.
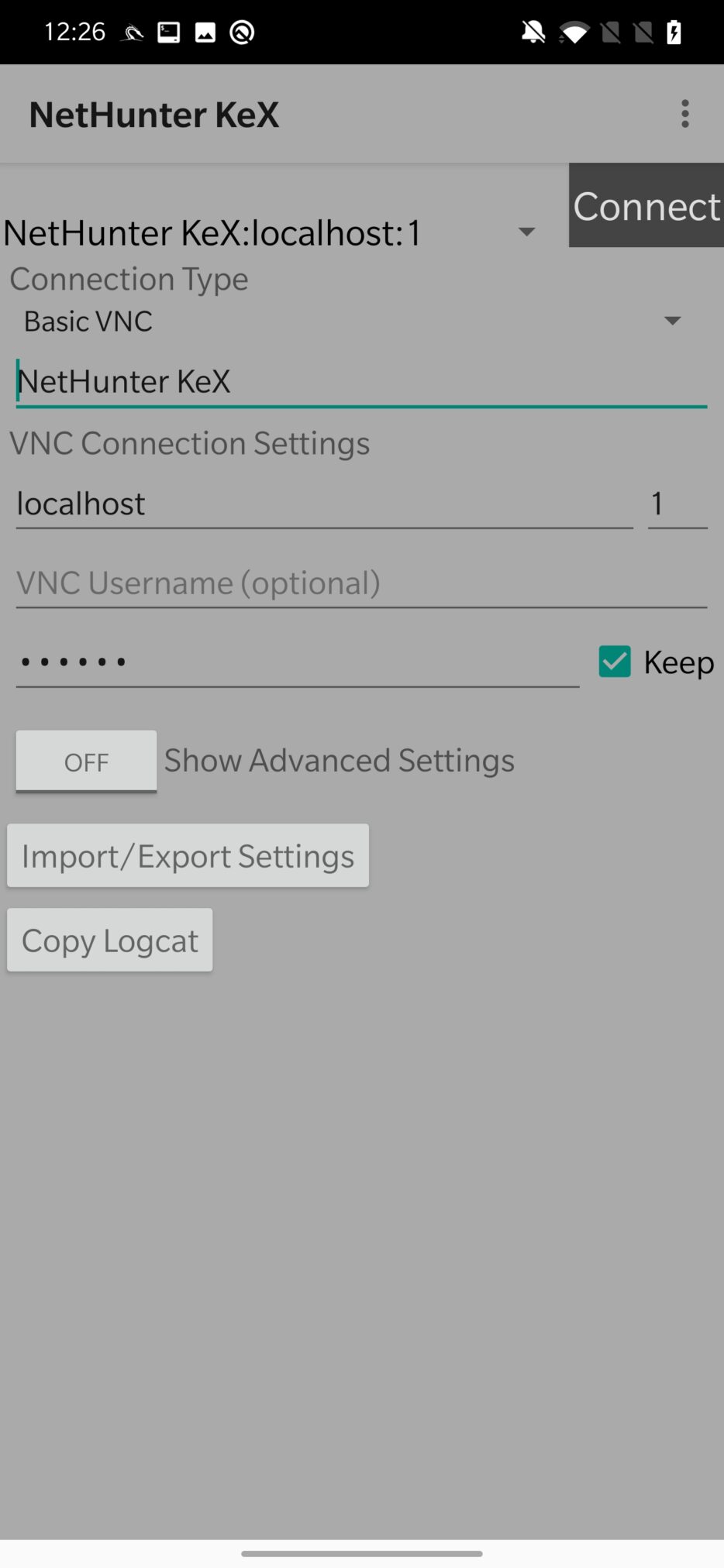
Once you have successfully created a local VNC connection, you can use your desktop Kali on Android. In the case there are missing some tools; I advise you to either install them manually or add necessary metapackages from Kali Chroot Manager.
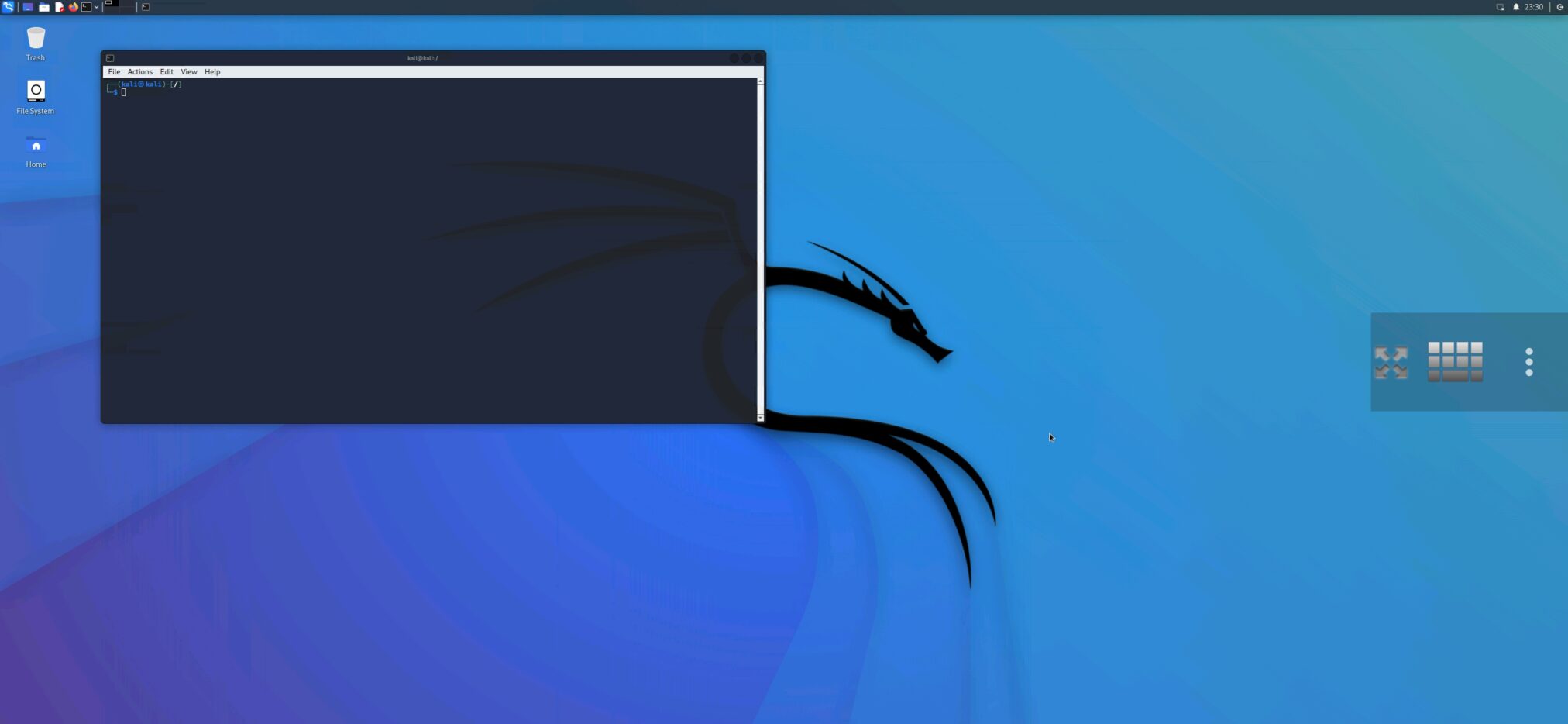
You can customize it via “three dots” option provided by the client app. Here it is possible to set the input mode, change the scaling, send extra keys and combinations, and disconnect from the session. If you quit the session, I advise to STOP SERVER in KeX Manger, so you don’t waste your smartphone resources.
USB Arsenal
A very important, USB Arsenal, allows you to emulate a range of USB devices and use them against a target system. This can be used to launch attacks, bypass authentication measures, and possibly gain access to the target system.
You can choose different targets such as Windows, Linux, and Mac OS. After you plug in an Android device to a targeted system, you can select from USB Function how your smartphone will be recognized by the operating system.
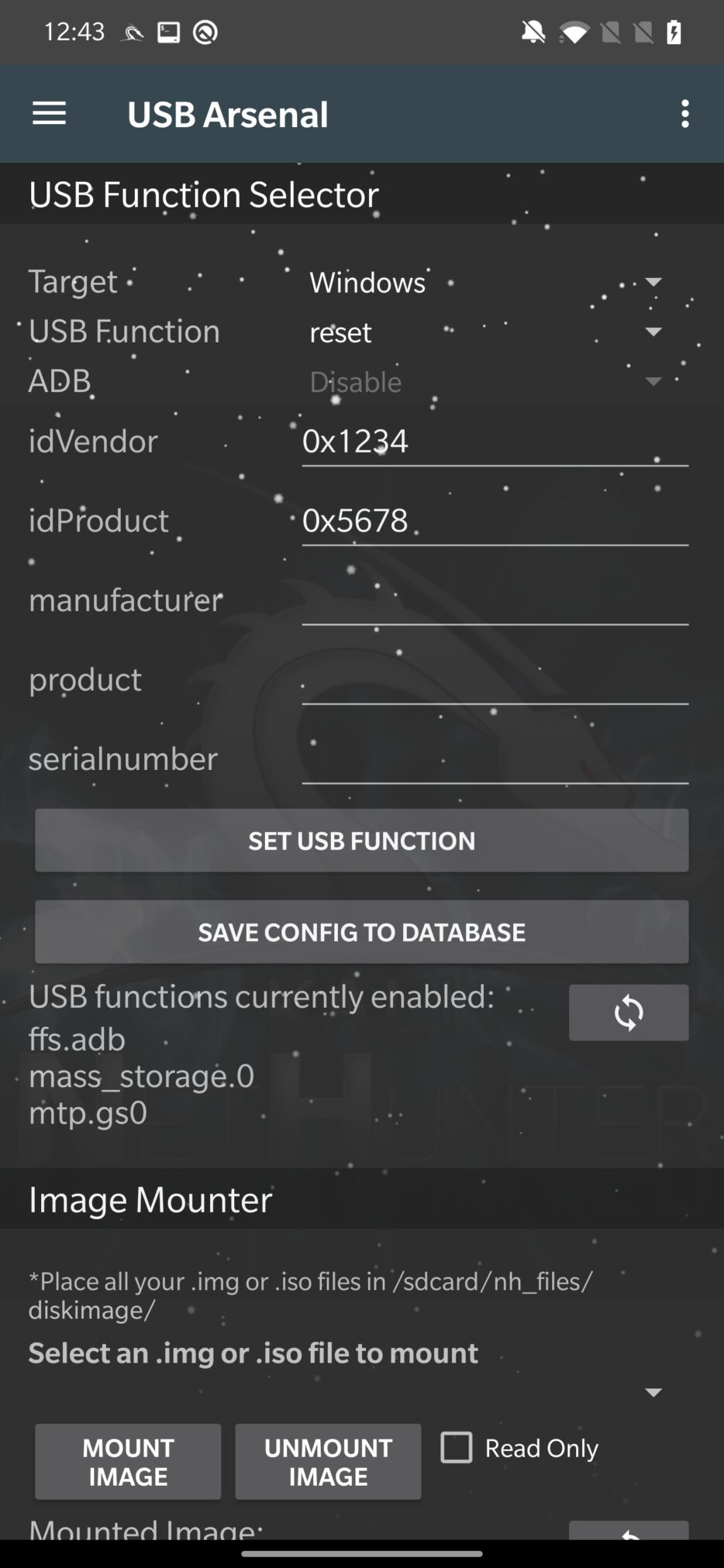
From the available functions, it can behave as, or as a combination of these options:
- hid – This function allows you to use your Android device as a Human Interface Device (HID). Using the HID tool can be a useful technique for injecting input into a target device that recognizes it as a keyboard or mouse. It is used for HID attacks and running Rubber Ducky scripts.
- mass_storage – It allows you to use a device as a mass storage device for file transfer.
- rndis – You can use a device as an RNDIS (Remote Network Driver Interface Specification) device. A host device can communicate with and control a remote device using the RNDIS communication protocol over a USB connection. Used for BadUSB and USB network tethering.
From further settings, it can enable or disable ADB commands and allows to set detail information about the device.
With Image Mounter you can choose a disk image from storage and mount it to a computer as if it were a real or virtual disk.
Conclusion
After reading this post, you should know how to change and customize MAC address for your interfaces, setup and use desktop Kali Linux on Android and how our device can behave differently after switching from various USB functions.
In upcoming blog we will focus entirely on how to setup NetHunter as BadUSB, how HID attacks works, test Rubber Ducky scripts and many more.

Thank you very much for your teachings, I am waiting for the next lessons
Thank you very much for lesson